SUID and SGID
Sometimes, unprivileged users must be able to accomplish tasks that require privileges. An example is the passwd program, which allows you to change your password. Changing a user’s password requires modifying the password field in the /etc/passwd file. However, you should not give a user access to change this file directly—the user could change everybody else’s password as well! Likewise, the mail program requires that you insert a message into the mailbox of another user, yet you should not give one user unrestricted access to another’s mailbox.
To get around these problems, Unix allows programs to be endowed with privileges. Processes executing these programs can assume another UID or GID when they’re running. A program that changes its UID is called a SUID program (set-UID); a program that changes its GID is called a SGID program (set-GID). A program can be both SUID and SGID at the same time.
When a SUID program is run, its effective UID (see Chapter 4) becomes that of the owner of the file, rather than of the user who is running it.
Sticky Bits
If a
program is SUID or SGID, the output of the
ls -l command will have the x
in the display changed to an s. If the program is
sticky, the last x changes to a
t as shown in Figure 6-3 and
Table 6-14.
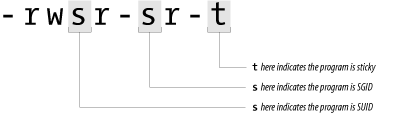
Figure 6-3. Additional file permissions
Table 6-14. SUID, SGID, and sticky bits
|
Contents |
Permission |
Meaning |
|---|---|---|
|
---s------ ... |
Get Practical UNIX and Internet Security, 3rd Edition now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

