Using Signed Requests to Secure a Data Connection
With a normal HTTP request sent via an application using the osapi.http methods, the container itself acts
as a proxy, forwarding any parameters passed through a request directly
to the server to which the request is being made without modifying them
(Figure 6-2).
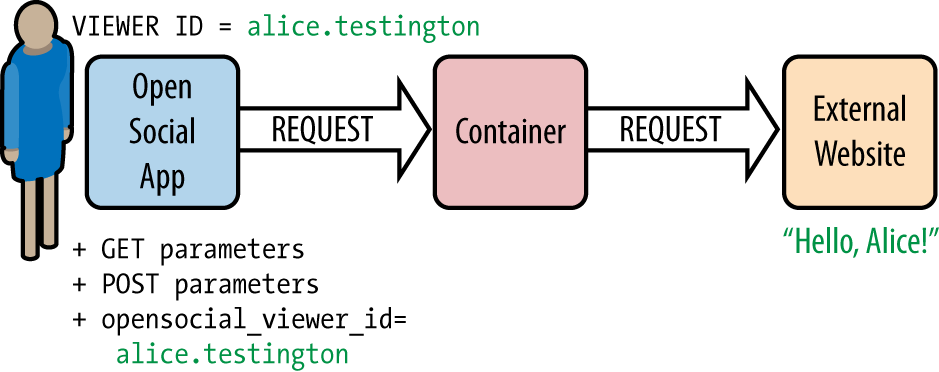
Figure 6-2. A user making a request to an external website through the container without OAuth authorization
When you’re collecting data from an external source where security is not an issue or where user validation is not a concern, this insecure method of data transference may suffice.
But let’s take a look at a different use case for making a request. Instead of just collecting some random insecure data, let’s say we are now making a POST request to a server to update the configuration information for a user. All of the parameters passed to the server are set within the application itself, including the user identifier. Since this request is completely exposed, a user simply running Firebug or modifying the request can spoof his identifier to alter or get information on a different user. Figure 6-3 shows the request to the server, which still appears completely valid despite the fact that a malicious user has now been granted access to information about another user.
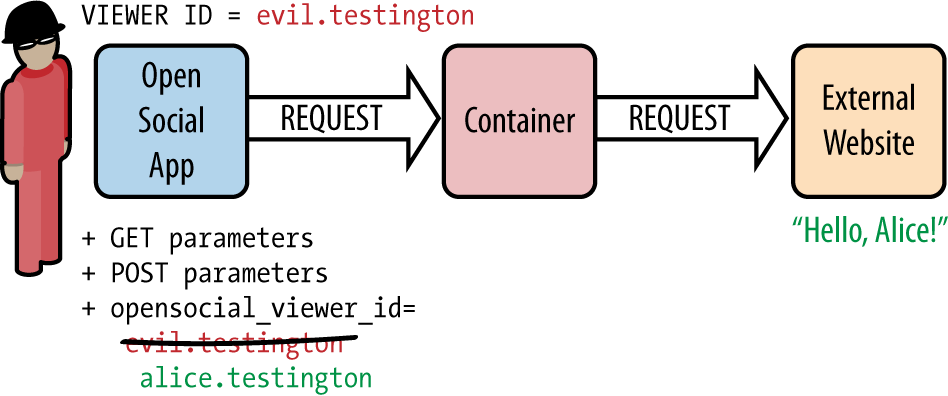
Figure 6-3. A ...
Get Programming Social Applications now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

