Step 2: Perform Discovery to Establish the Endpoint URL
The process of performing discovery on an OpenID provider identifier will take us through a couple of substeps, both involving communication between the relaying party and the OpenID provider. Our goal in this stage is to perform discovery on the OpenID identifier to:
Determine whether the OpenID identifier is valid.
If it is valid, extract the endpoint URL to which the user will be forwarded for authentication.
This exchange is demonstrated in Figure 11-2.
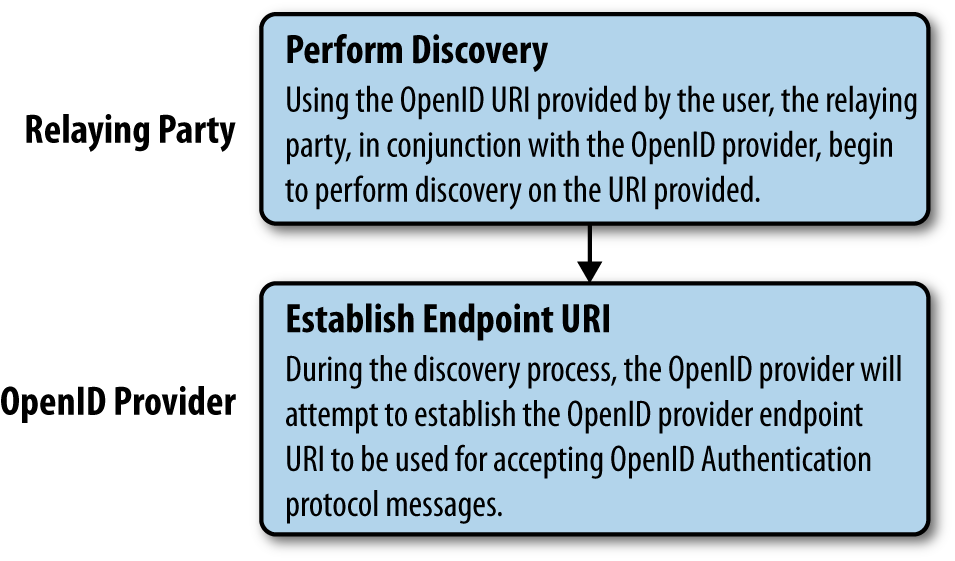
Figure 11-2. OpenID, step 2: Relaying party performs discovery on OpenID identifier
Using the normalized URL from the last step, the relaying party will make a request to the provided OpenID identifier URL. If the identifier is valid, the provider will respond with the endpoint URL that is used either to redirect the user or to request the markup that sends the user through the authentication step.
Get Programming Social Applications now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

