Advanced Configuration
The steps performed so far have used the standard administrative tools in Windows NT. Now it’s time to work on some more advanced tasks to further enhance the security of your system. These tasks include:
Encrypting the password database
Editing the registry
Disabling unnecessary files
Protecting the System Accounts Database
If an attacker gets hold of a system backup or an emergency repair disk, he could use a tool such as L0phtCrack to run a dictionary attack or a brute force attack on the Systems Account Manager (SAM) database. However, if the password hashes in the database are encrypted, these attacks will be unsuccessful.
In NT 4.0 Service Pack 3, Microsoft introduced a facility for encrypting the password hashes stored in the SAM database. This facility protects the database from offline password cracking attempts. To implement this encryption feature, run the following command:
C:\> syskey
Running syskey brings up the dialog box shown in
Figure 2.5. Note that enabling password encryption
is a one-way operation—once it is enabled, it cannot be
disabled.
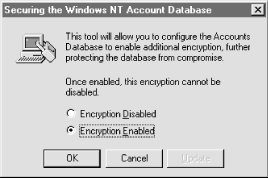
Figure 2-5. The syskey command encryption dialog box
When you enable encryption, the system creates a random 128-bit encryption key. This is used to encrypt the password hash entries in the SAM database in the registry (HKLM\SAM). The encryption key is protected with another key, called the system key ...
Get Securing Windows NT/2000 Servers for the Internet now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

