If you’ve carefully followed the installation and configuration steps outlined in Chapter 2, and Chapter 3, your bastion host is now quite secure. However, there is no way of administering it remotely!
NT’s standard remote administration tools such as Event Viewer and Server Manager are based on RPC using NetBIOS. The problem with NetBIOS (as I discussed in Chapter 1) is that it’s considered unacceptably unsecure in perimeter networks. Hence, we must find alternative tools for administering and monitoring the Windows NT host.
The basic requirements for any new remote management tools are:
- Authentication
Both user and source IP address authentication are required to restrict unauthorized access to the servers. IP address authentication means access to certain services can be allowed or rejected based on the IP address of the client.
- Encryption
Since we are performing administrative tasks, such as adding users and changing passwords, all sessions must be encrypted.
- Ability to use the Windows NT GUI tools
It’s not possible to perform all administration tasks using the command prompt. Hence, we need some kind of remote graphics console.
- Ability to transfer files from and to the remote system
It’s often important to be able to transfer files to your bastion hosts in a simple way.
This chapter presents three different solutions for remote management of Windows NT/Windows 2000 servers:
- Symantec pcAnywhere v9.x
A very popular commercial software package that works on both Windows NT 4.0 and Windows 2000 systems.
- Windows 2000 Terminal Services
A remote management solution that is available on Windows 2000 Servers only (not Windows 2000 Professional).
- A combination of open source software
This is a free alternative based on the following components:
- Secure Shell (SSH)
A set of Unix programs that allow you to log on to and execute commands on a remote computer. SSH provides a user authentication mechanism and performs session encryption.
- TCP Wrappers
A set of Unix programs that log incoming connection requests and provide IP address-based access control, ensuring that the connecting host has permission to connect to a service before giving access to that service.
- Cygwin
A free Win32 porting layer for Unix applications. Cygwin enables us to compile and run the SSH and TCP Wrappers Unix source code on the Win32 platform.
- Virtual Network Computing (VNC)
A client and display server combination that provides a graphical user interface over the network.
SSH is an effective authentication service. The drawback is that it’s strictly text-based. However, by using it in conjunction with TCP Wrappers and VNC, a powerful, secure, and platform-independent remote administration solution is achieved. It can be somewhat tricky to get this solution running on Windows NT the first time, but if you carefully follow the instructions provided later in this chapter, you’ll be up and running in no time.
This chapter walks you through the necessary steps to successfully install and configure these three recommended remote management solutions.
Symantec’s pcAnywhere product has become the de facto standard remote console solution on Windows NT. It has many features and good security options (128-bit RC4 encryption using the MS CryptoAPI and host IP address authentication), and it’s relatively easy to configure and use. It also includes an excellent file transfer client. A sample pcAnywhere session is shown in Figure 4.1.
pcAnywhere uses one well-known TCP port (tcp/5631) for remote sessions. Another well-known port (udp/5632) is used to query the status of remote hosts. You only need to allow tcp/5631 from your management clients to your bastion hosts through your firewalls.
A pcAnywhere license costs about $170 if you buy it online from Symantec.
This section explains the special configuration steps you must perform when installing pcAnywhere 9.x on a bastion host:
Start the installation.
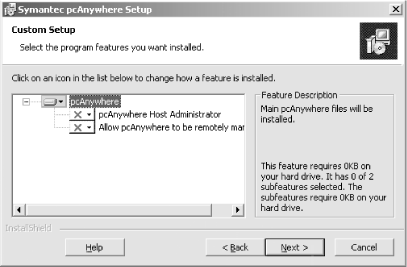
Use the custom installation method and deselect the two optional components, shown in Figure 4.2.
Reboot the system when prompted to do so.
When the system has rebooted, log on and click on the “Symantec pcAnywhere” shortcut on the Start menu.
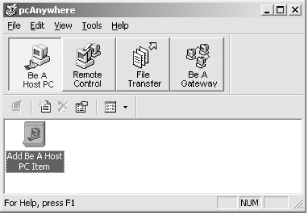
pcAnywhere runs a Setup wizard the first time it starts. Cancel the wizard and delete all items in the “Be a Host PC” view, as shown in Figure 4.3.
Create a new Host PC item by double-clicking on the “Add Be A Host PC Item” wizard. Use “TCP/IP” as the connection device, enable pcAnywhere Caller Security, and add a pcAnywhere user. Uncheck the “Automatically launch this host upon wizard completion” checkbox.
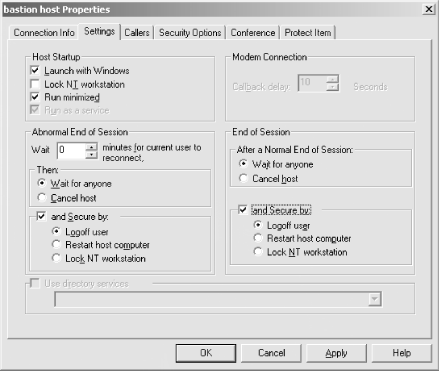
Bring up the Properties dialog box for the newly created Host PC item and click on the Settings tab, shown in Figure 4.4.
Configure the Host PC item to use the non-default settings shown in Table 4.1.
Table 4-1. Recommended pcAnywhere Host PC Settings
|
Setting |
Description |
Recommended Value |
|---|---|---|
|
Launch with Windows |
Configures the pcAnywhere Service to start this Host PC at boot |
Yes |
|
Abnormal End of Session Security |
Specifies the action to take if an ongoing connection is terminated unexpectedly |
Logoff user |
|
End of Session Security |
Specifies the action to take when a pcAnywhere session ends |
Logoff user |
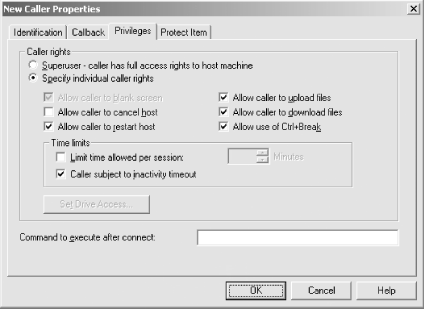
Add any additional user accounts using the Callers tab. Configure fine-grained user privileges in the “Privileges” tab, for each individual user, as shown in Figure 4.5.
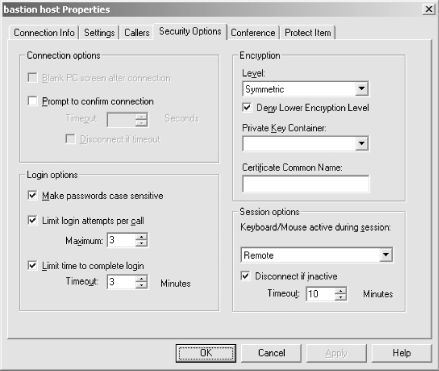
Configure the non-default settings listed in Table 4.2 in the Security Options tab of the Host PC item, as shown in Figure 4.6.
Table 4-2. Recommended Security Settings for pcAnywhere
|
Setting |
Description |
Recommended Value |
|---|---|---|
|
Encryption Level |
Configures the level of encryption used by pcAnywhere sessions |
Symmetric/Deny Lower Encryption Level |
|
Make passwords case sensitive |
Controls whether the case (upper- or lowercase) of passwords is significant |
Yes |
|
Keyboard/mouse active during session |
Controls where input is allowed |
Remote |
|
Disconnect if inactive |
Specifies when an inactive session should be terminated |
10 minutes |
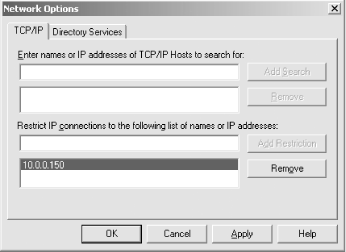
Configure IP address restrictions. Click on Tools → Network Options (shown in Figure 4.7), and add the hosts that should be allowed to access this computer over the network.
The last GUI-based configuration step is to enable logging. Logging can be configured by selecting “Logging options” from the Tools menu. I recommend that you enable NT Event logging for all pcAnywhere events.
There are a number of pcAnywhere settings in the registry that should be changed from their defaults on a bastion host.
The pcAnywhere client can be configured to discover hosts on a subnet automatically. The following setting controls whether or not a server should respond to pcAnywhere discovery broadcasts to make itself known to a client. Usually, broadcasts in the perimeter aren’t allowed, so disable this feature by configuring the following registry value on your servers:
|
Value Name |
Type |
Recommended Value |
|---|---|---|
|
HKLM\SOFTWARE\Symantec\pcANYWHERE\CurrentVersion\System\DisplayHostInList |
REG_DWORD |
0 |
Older versions of pcAnywhere used a different set of TCP (tcp/65301) and UDP (udp/22) ports. Later versions of pcAnywhere support these ports, as well as the new ones, for backward compatibility. You can disable the old ports by adding the following registry value:
|
Value Name |
Type |
Recommended Value |
|---|---|---|
|
HKLM\SOFTWARE\Symantec\pcANYWHERE\CurrentVersion\System\TCPIPPortCompatibility |
REG_DWORD |
0 (this is the default in v9.2) |
A pcAnywhere client tries to query the server for its status using UDP before trying to connect to it. If you only allow tcp/5631 from the management clients through your firewall, this causes the client to give up after not being able to query the status. You can configure the client to try to connect anyway by changing the following setting on the pcAnywhere client:
[38] You can download the High Encryption Pack from http://www.microsoft.com/windows/ie/download/128bit/intro.htm (for NT 4.0), or http://www.microsoft.com/windows2000/downloads/recommended/encryption/default.asp (for Windows 2000)
Get Securing Windows NT/2000 Servers for the Internet now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.