Performing Third-Party Audits
How do you know that your perimeter network’s design and implementation is as secure as possible? Maybe there’s something that has been overlooked, or maybe a configuration error has been made somewhere.
It’s usually a good idea to have a trusted third party perform annual audits of your perimeter network. There are two approaches to perimeter network security testing: “black-box” vulnerability scanning, and the “white-box” design review audit. I recommend using someone from outside your organization to perform the initial network security audit or vulnerability analysis. There are companies that specialize in performing network security audits.
The Black-Box Approach
In the black-box approach, the tester is provided only with a range of IP addresses to scan and probe for known vulnerabilities, much as a hacker would. System information and network diagrams might not even be disclosed. The only way to perform a test in this manner is to scan and probe all IP addresses in the range for active services, and then probe the active services for vulnerabilities. This approach is often referred to as vulnerability scanning and is illustrated in Figure 7.1.
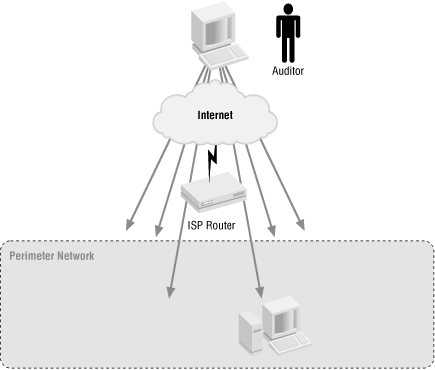
Figure 7-1. The black-box audit
Commercial scanning tools include:
- Axent’s NetRecon
Available at http://www.axent.com/
- Cisco Secure Scanner (formerly NetSonar).
Available at http://www.cisco.com/
- Cybercop ...
Get Securing Windows NT/2000 Servers for the Internet now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

