CHAPTER 17
Summary and the Future of Security Patterns
The part can never be well unless the whole is well.
Plato
We complete our book with tables of patterns, a list of research directions, some principles for security and a look at the future.
17.1 Summary of Patterns
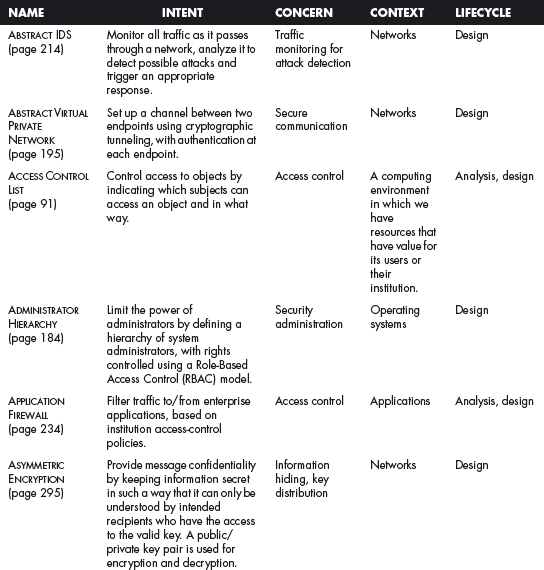
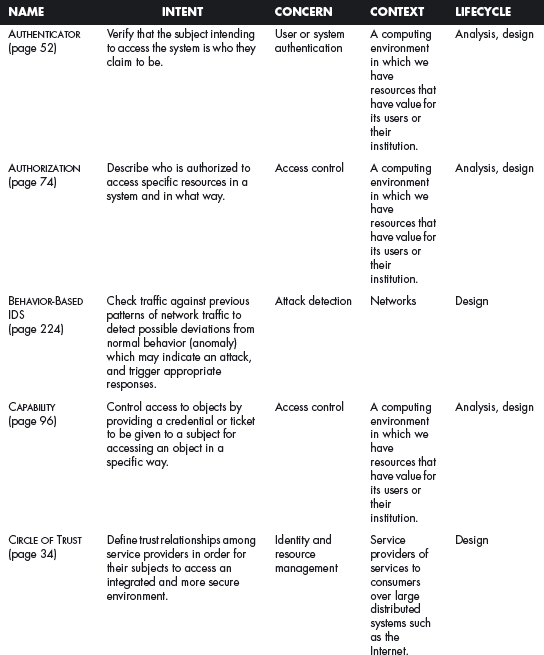
This section offers a table that summarizes all the patterns in this book. For each pattern we have listed its classification using four of the dimensions described in Chapter 2. The Intent indicates what problem is solved by the pattern, the concern is its basic type of intended function, the context describes the environment where it can be applied or the prerequisites for its use, and lifecycle indicates in what stage of the development lifecycle the pattern is useful. Other dimensions could be added, but they would clutter this table. Ideally, a complete description of each pattern should be implemented in a tool that could present the designer with the relevant patterns according to the step of the design.
We first list the security patterns presented in this book, then (page 489) the misuse patterns in the book. We have written several other security patterns, described on page 490. Finally, we security patterns under development (page 493).
Security Patterns Described in this Book
Misuse Patterns Described ...
Get Security Patterns in Practice: Designing Secure Architectures Using Software Patterns now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

