SELinux Policy Syntax
The railroad diagram in Figure 6-9 represents an overview of the syntax of an SELinux policy.
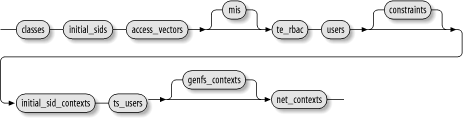
Figure 6-9. The SELinux Policy
As the figure shows, an SELinux policy consists of 11 elements, several of which are optional:
-
classes Defines the security object classes recognized by SELinux.
-
initial_sids Defines initial SIDs for important security objects.
-
access_vectors Defines access vectors associated with each security object class.
-
mls Defines MLS configuration (optional).
Tip
MLS is not currently implemented in sample SELinux policies and is not covered in this book.
-
te_rbac Defines type enforcement and role-based access control configuration.
-
users Defines the user configuration.
-
constraints Defines constraints that the security policy must observe (optional).
-
initial_sid_contexts Defines the security contexts of important security objects.
-
fs_use Defines the method of labeling of filesystem inodes.
-
genfs_contexts Defines security contexts for filesystems lacking persistent labels (optional).
-
net_contexts Defines security contexts for network objects.
The policy elements must appear in the order indicated by the railroad diagram. However, you generally don’t have to concern yourself with the order of policy statements, because each type of statement resides in a designated file or directory. As explained in Chapter 4, the SELinux policy Makefile assembles ...
Get SELinux now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

