2.1. Principles of Operation
This first section describes the fundamental transparent bridge algorithms. The presentation here is primarily from a behavioral perspective, that is, how the bridge behaves in response to received frames.
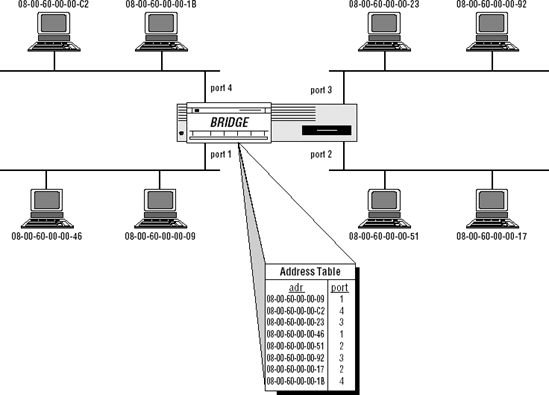
Figure 2-1 depicts a simple bridged LAN configuration.
Note that:
There are multiple, distinct LAN segments interconnected by the bridge. (The figure shows four such segments, but there is no architectural limit on the number of LANs that may be interconnected by a single bridge.)
Each station has a globally unique 48-bit unicast address. This is critical; proper bridge operation depends on the use of globally unique addresses at the link layer.
The bridge has a port, or interface, on each of the LANs to which it connects.
There is a table within the bridge that maps station addresses to bridge ports; that is, the bridge knows through which port each station can be reached.
The bridge operates in promiscuous mode; that is, it receives (or at least attempts to receive) every frame on every port, regardless of the destination address (target) of the frame. A typical end station will only attempt to receive those frames whose destination address matches that of the station; in contrast, a bridge receives all frames regardless of the intended destination.
Figure 2.1. Bridged LANs[]
[] In this figure, and in many others in this book, LANs are depicted as ...
Get The All-New Switch Book: The Complete Guide to LAN Switching Technology, Second Edition now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

