Chapter 7. Security for Virtual Environments: Guarding the Treasure
What Is Security for Virtual Environments?
There are two segments of the Kusnetzky Group Model that cut across all of the functional segments. Security and management for virtual environments protect and manage all of the other layers. This time, we’re going to examine security for virtual environments (see Figure 7-1). Security for virtual environments refers to the tools necessary to control access to and use of all of the other layers of virtualization technology.
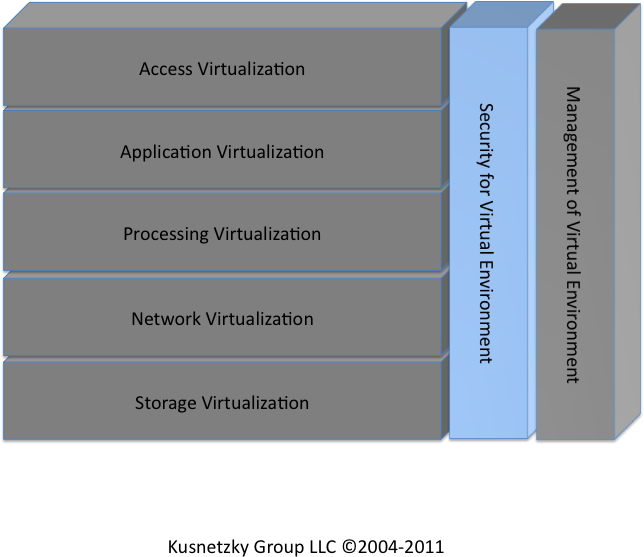
Depending upon the approach, security can require a small piece of software, often called an agent, to be added to each virtual resource. This, of course, can be quite a task in itself. This approach also means that part of each system’s time is spent doing security processing. If we consider a physical system supporting 40 virtual servers, each of which is supporting multiple workloads and communicating to thousands of client systems, the task of installing and maintaining all of that security software could be an overwhelming task.
Other suppliers have developed a different approach. Their approach is to capture the stream of network communication going from server to server, from application to application, from storage device to server, and funnel it through a separate security appliance server. This way, ...
Get Virtualization: A Manager's Guide now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

