Chapter 4. Auditing, Monitoring, and Securing
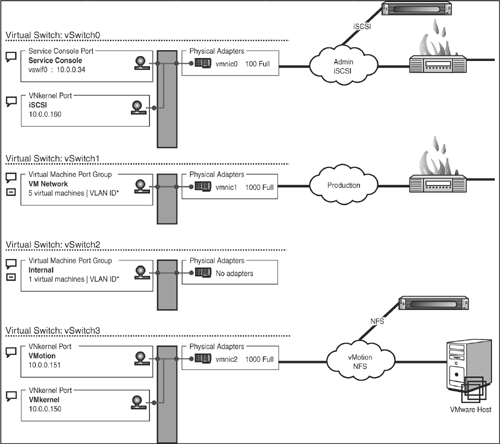
Is ESX secure? That is the number one question to be answered by this chapter, and the question petrifies security specialists every time ESX is brought into the mix of equipment and software. This is because ESX is a large unknown with regard to security as ESX was designed to be placed behind a firewall. Specifically, access to any ESX Server Ethernet port is intended to be made through a firewall, as shown in Figure 4.1. Figure 4.1 depicts the basic ESX networks and the need for multiple firewalls for each exposed network.
Figure 4.1. ESX Server behind a firewall
However, here we are about to discuss ...
Get VMware ESX Server in the Enterprise: Planning and Securing Virtualization Servers now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

