Message Digest Functions
Message digest functions distill the information contained in a file (small or large) into a single large number, typically between 128 and 256 bits in length. This is illustrated in Figure 10.3. The best message digest functions combine these mathematical properties:
Every bit of the message digest function is influenced by every bit of the function’s input.
If any given bit of the function’s input is changed, every output bit has a 50 percent chance of changing.
Given an input file and its corresponding message digest, it should be computationally infeasible to find another file with the same message digest value.
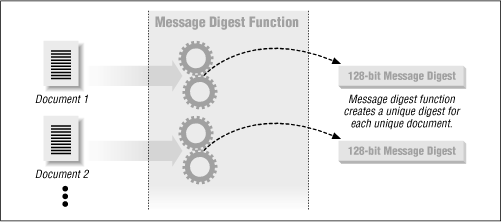
Figure 10-3. A message digest function
Message digests are also called one-way hash functions because they produce values that are difficult to invert, resistant to attack, mostly unique, and widely distributed.
Many message digest functions have been proposed and are in use today. Here are just a few:
- HMAC
The Hashed Message Authentication Code, a technique that uses a secret key and a message digest function to create a secret message authentication code. The HMAC method strengthens an existing message digest function to make it resistant to external attack, even if the message digest function itself is somehow compromised. (See RFC 2104 for details.)
- MD2
Message Digest #2, developed by Ronald Rivest. This message digest is the most secure of Rivest’s ...
Get Web Security and Commerce now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

