On the security front, Windows 7 has streamlined several features found in Windows Vista, making them much more accessible and less irritating in this new version of Windows. For example, the infamous User Account Control (UAC) is one of the most annoying features in Vista. In this version of Windows, Microsoft has tweaked UAC so that it interrupts users only when needed. Microsoft has also replaced the Security Center in Vista with the new Action Center in Windows 7, which focuses not just on displaying problems, but also on offering suggestions and solutions to solve problems. The Credential Manager now has the ability to back up its credential information to a file. In addition, Enterprise and Ultimate users can now encrypt a portable thumb drive using BitLocker To Go.
In Windows 7, Microsoft has designated the new Action Center as the one-stop place to find all your system maintenance and security messages. The key design goal of the Action Center is to help users solve system issues quickly and conveniently.
The system tray is now less cluttered, compared with its appearance in previous versions of Windows—it now has four main icons: Action Center, Network, Speaker volume, and Date and Time (see Figure 4-1). Mobile computers will have a power icon as well.
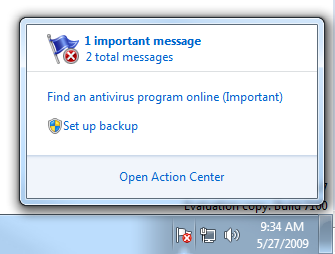
In particular, the Action Center icon (represented as a white flag, which will include a red “x” if there are important messages requiring your attention) replaces several notification icons from Vista, reducing much clutter. When you click the Action Center icon, a pop-up window displays a summary of system messages of varying importance levels. In addition, it also provides a way for you to resolve the error. For example, Figure 4-2 shows that I have two messages for my computer—one important and one normal. The pop up also includes two links for me to resolve my problems—one to find an antivirus program and one to set up a backup for my computer. To view the messages, click the message icons or click the Open Action Center link.
The Action Center will display the details of the messages along with a button to help you solve the issue.
Besides displaying messages on maintenance and security-related issues, the Action Center can also help you troubleshoot problems with your computer and restore your computer to its setup from an earlier time.
Messages are classified into two main categories: Security and Maintenance. Security messages relate to issues concerned with:
Windows Update
Internet security settings
Network firewall
Spyware and related protection
User Account Control
Virus protection
Maintenance messages relate to issues concerned with:
Windows Backup
Windows Troubleshooting
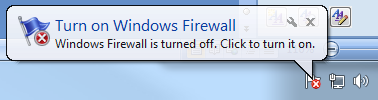
Messages can be important or normal. Important messages display notification balloons (see Figure 4-3) in the System tray in addition to appearing in Action Center. A good example of an important message balloon is what happens when the Windows Firewall is turned off.
In the Action Center, you can also expand on each message category to view the status of each Security- and Maintenance-related item for your computer.
Note
The Action Center is for displaying messages and resolving problems, not managing tasks. For example, you can use the Action Center to help you find an antivirus program, but you cannot manage your Windows Firewall in the Action Center.
You have the option to prevent messages from displaying by clicking the Change Action Center settings link in the left side of the Action Center window. Uncheck the item(s) for which you do not want to view a message.
Get Windows 7: Up and Running now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.