Security Monitoring
A key element of effective network security is security monitoring. Good security is an ongoing process. Following the security guidelines discussed earlier is just the start. You must also monitor the systems to detect unauthorized user activity and to locate and close security holes. You need to know the system in order to detect and fix these problems as they arise.
Windows NT provides system monitoring through the Event Viewer. Most Windows NT administrators are familiar with the Event Viewer from debugging problems that occur during system startup or from fixing problems with newly installed hardware. An equally important function for the Event Viewer is security monitoring. To perform this important task you must first define the audit policy for your system. Open the User Manager for Domains and select Audit from the Policies menu. This opens the Audit Policy windows shown in Figure 12-4. Use this window to define your security monitoring policy.
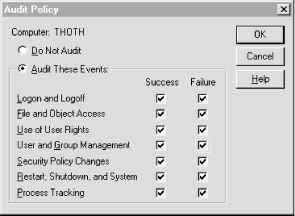
Figure 12-4. Setting an Audit Policy
Network security is monitored by examining the event logs of individual systems on the network. To detect unusual activity on a system, you must know what activity is normal. You need to know this in order to develop a feel for how things should be. Through the Audit Policy window you can enable the following audits that give you insight into the normal activity of your system: ...
Get Windows NT TCP/IP Network Administration now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

