Chapter 15. Issuing Certificates
Having created the required certificate templates, the next step is to determine how to get the certificates to the desired computers, users, or network devices.
A certificate request involves actions performed at the computer where the certificate request is generated and at the certification authority (CA) that issues the certificate to the requestor.
When a certificate request is initiated, the process shown in Figure 15-1 takes place.
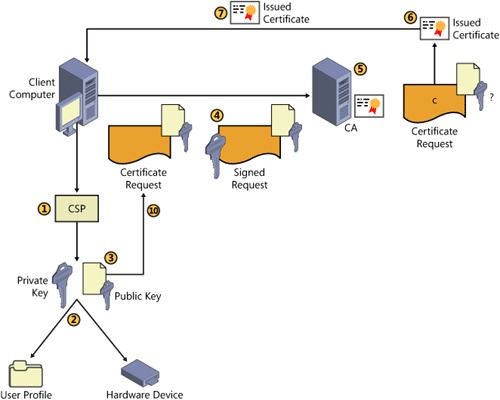
Figure 15-1. The certificate enrollment process
When the user generates a request for a certificate, the client computer asks the cryptographic service provider (CSP) designated by ...
Get Windows Server® 2008 PKI and Certificate Security now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

