Chapter 13. Managing Computer Security
Chapter at a Glance
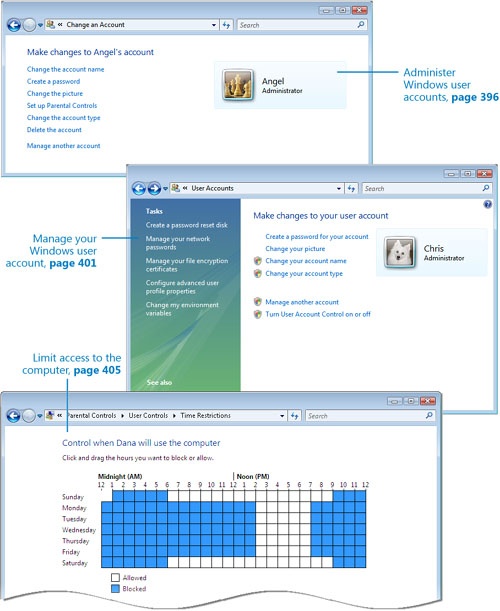
In this chapter, you will learn to: | |
✓ | |
✓ | |
✓ | Limiting Access to the Computer, to Programs, and to the Internet. |
✓ | |
✓ | |
In the old days, computers were isolated from each other, and the only way to transfer information among them was on a floppy disk (now referred to as "sneaker net"). With the advent of networks, information transfer became easier, but so did the possibility that the information stored on a computer would be accessed inappropriately or even illegally ...
Get Windows Vista® Step by Step Deluxe Edition now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

