Chapter 3. The MAC
If you cannot get rid of the family skeleton, you might as well make it dance.
Most of the work in the 802.11ac MAC is evolutionary. In contrast with the major efficiency enhancements introduced in 802.11n, most of the MAC work in 802.11ac consists of supporting new physical layer features. Frames are bigger, but the aggregation framework in place handles those larger frames without significant change. One of the few protocol features to see large changes was around sharing radio resources between channels of different sizes.
Framing
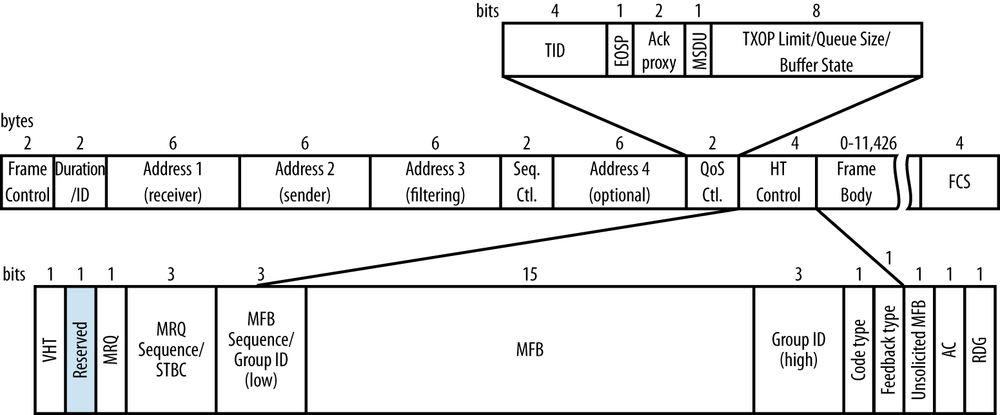
For the most part, 802.11ac maintains the frame format used by its predecessors. There are two major changes, shown in Figure 3-1. First, 802.11ac extends the maximum frame size from almost 8,000 bytes to over 11,000 bytes, further increasing the ability to aggregate frames from higher layers. Second, it reuses the HT Control field from 11n, but does so by defining a new form of the Control field. When the HT Control field begins with a 0, the format is identical to 802.11n and the HT Control field is of the HT-variant type.[21] When the HT Control field begins with a 1, the HT Control field is of the VHT-variant type. Figure 3-1 shows the format of the VHT-variant HT Control field. It is composed of fields that are used to communicate MCS feedback, a seldom-implemented procedure that enables two devices to exchange information on how well transmissions are received to find the best data rate for the connection.
Frame Size and Aggregation
Frame aggregation was introduced in 802.11n to improve network efficiency. As with many network protocols, one of the biggest sources of overhead in 802.11 is acquiring the channel for the right to transmit. Aggregation works to decrease the relative amount of overhead by allowing a device to obtain access to the radio channel and then using that opportunity to transmit multiple frames.[22] 802.11 standards are not prescriptive and define only the aggregate frame format. Implementing aggregation requires that a device look ahead through its transmit queue to find frames to coalesce into a single aggregate frame, and each vendor’s implementation may be slightly different.
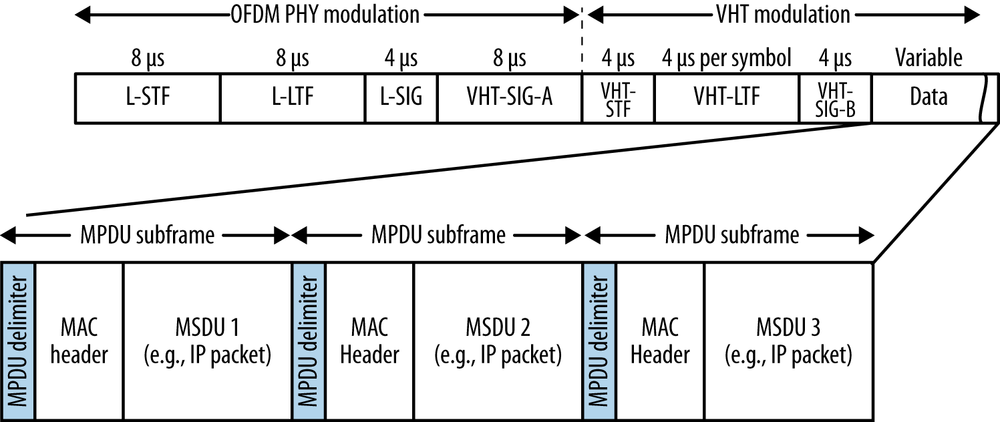
802.11ac, however, adds an interesting new take on aggregation: all frames transmitted use the aggregate MPDU (A-MPDU) format. Even a single frame transmitted in one shot is transmitted as an aggregate frame. Moving to an all-aggregate, all-the-time transmission model means that the 802.11ac MAC must take over all the framing responsibility, and the physical layer works only with the total length of what it transports.
Note
All 802.11ac data frames are sent in an A-MPDU, even if the A-MPDU has only one frame in it.
It might seem at first glance that transmitting every frame as an A-MPDU, regardless of the content of the data, would not be efficient. However, due to the potentially high speeds in 802.11ac, simply describing the length of the frame requires a large number of bits. The maximum transmission length is defined by time, and is a little less than 5.5 milliseconds. At the highest data rates for 802.11ac, an aggregate frame can hold almost four and a half megabytes of data. Rather than represent such a large number of bytes in the PLCP header, which is transmitted at the lowest possible data rate, 802.11ac shifts the length indication to the MPDU delimiters that are transmitted as part of the high-data-rate payload.[23]
Figure 3-2 shows the format of the A-MPDU aggregation type. The maximum length of an A-MPDU is controlled by the value of a field called the Maximum A-MPDU Length Exponent, which describes the maximum length of an A-MPDU by the formula 213+Exponent–1 bytes. 802.11ac allows values for the exponent ranging from 0 to 7, which allows the maximum A-MPDU length to range from 8 KB to 1 MB.[24] Table 3-1 compares the amount of data that can be transmitted at various points in the protocol stack by the 5 GHz–capable 802.11 physical layers.
| Attribute | 802.11a | 802.11n | 802.11ac |
| MSDU (MAC payload) size | 2,304 | 2,304 | 2,304 |
| MPDU (MAC frame) size | Implied by maximum MSDU size | Implied by A-MSDU size | 11,454 |
| A-MSDU (aggregate MAC payload) size | Not used with 802.11a | 7,935 | Implied by maximum MPDU size |
| PSDU (PLCP payload) size | 4,095 bytes | 65,535 bytes | 4,692,480 bytes |
| PPDU (PLCP frame) size | Implied by maximum PSDU size | 5.484 ms (mixed mode) or 10 ms (greenfield mode) | 5.484 ms |
Management Frames
Management frames signal that they are capable of building an 802.11ac network or participating in an 802.11ac network by including the VHT Capabilities Information element. This element is placed in Probe Request and Probe Response frames to enable client devices to match their capabilities to those offered by a wireless network.
The VHT Capabilities Information element
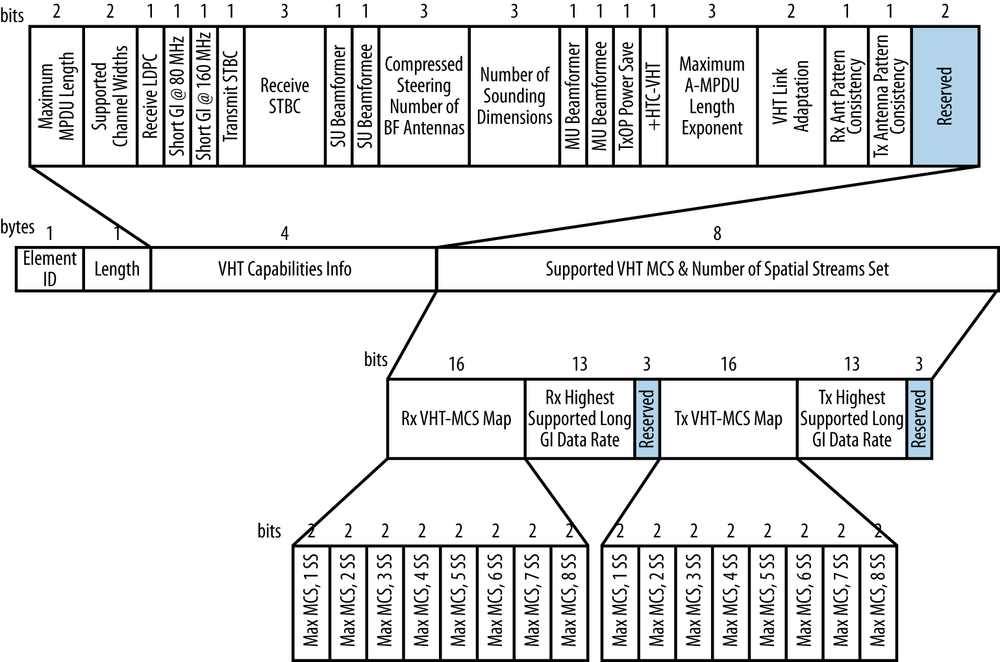
The VHT Capabilities Information element, shown in Figure 3-3, is the core information element used in management frames to set up operation of 802.11ac networks. It has a simple structure, consisting of two fields that describe the protocol features supported by the transmitter and the speeds that the transmitter is capable of using.
Within the VHT Capabilities Info element, the fields are:
- Maximum MPDU Length (2 bits)
MAC frames in 802.11ac may have one of three lengths: 3,895 bytes, 7,991 bytes, or 11,454 bytes. Those three lengths correspond to values of 0, 1, and 2 in this field. The value of 3 is reserved.
- Supported Channel Width set (2 bits)
802.11ac devices are required to support 20 MHz, 40 MHz, and 80 MHz operation. This field is used to indicate support for 160 MHz operation. It takes on the value 0 if there is no 160 MHz support, the value 1 if the transmitter supports 160 MHz contiguous operation only, and the value 2 if it supports both 160 MHz contiguous operation and 80+80 MHz operation. The value 3 is reserved.
- Rx LDPC (1 bit)
This field is set to 1 if the transmitter can receive LDPC-encoded frames.
- Short GI for 80 (1 bit) and Short GI for 160 & 80+80 (1 bit)
These fields are each set to 1 if the transmitter can receive frames transmitted using the short guard interval with the indicated channel bandwidth. See Guard Interval for more details.
- Tx STBC (1 bit)
This field is set to 1 to indicate that transmission of STBC-coded frames is supported.
- Rx STBC (3 bits)
This field describes how many spatial streams are supported for reception of STBC-coded frames. It may be set to 0, 1, 2, 3, or 4, describing the maximum number of spatial streams supported on reception.[25] For support of one spatial stream, the field takes the value 1. The value 0 is used to indicate that STBC is not supported, and the values 5–7 are reserved.
- Single-User (SU) Beamformer (1 bit) and Beamformee (1 bit)
When set to 1, these fields indicate that the transmitter is capable of operating as a single-user beamformer or beamformee that exchanges packets with one other station. This feature will be discussed in Chapter 4.
- Compressed Steering Number of Beamformer (BF) Antennas (3 bits) and Number of Sounding Dimensions (3 bits)
These fields are used in the channel measurement process for beamforming to indicate the maximum number of antennas that can participate in channel measurement, and will be described more fully in Chapter 4.
- Multi-User (MU) Beamformer (1 bit) and Beamformee (1 bit)
When set to 1, these fields indicate that the transmitter is capable of operating as a multi-user beamformer or beamformee.
- VHT TxOp Power-Save (1 bit)
An AP can set this bit to 1 to enable power save operations during a VHT transmission burst, or 0 to disable them. Stations associating with a network will set this bit to 1 to indicate the capability is enabled or 0 if it is disabled.
- +HTC-VHT capable (1 bit)
This value is set to 1 to indicate that the transmitter is capable of receiving the VHT-variant HT Control field.
- Max A-MPDU Length Exponent (3 bits)
This field can take on the values 0–7 and is used to communicate the size of the A-MPDU that may be transmitted. The effects of its values are described in Frame Size and Aggregation.
- VHT Link Adaptation capable (2 bits)
This field is used for link adaptation feedback to select the most appropriate MCS for a link using explicit feedback.
- Receive and Transmit Antenna Pattern Consistency (1 bit each)
These bits are each set to 1 if the antenna pattern of the transmitter does not change after association completes, and 0 otherwise. One of the most common reasons for an antenna pattern to change is beamforming.
Following the Capabilities element is the Supported MCS Set element, shown at the bottom of Figure 3-3. It is split into two identical halves, with the first half describing the receiving capabilities and the second half describing the transmission capabilities. It contains the following fields:
- Rx and Tx VHT-MCS Map (16 bits each)
The MCS map is a simple structure. Two bits are used to represent three options: the value 0 stands for the mandatory minimum support of MCS 0 through 7, the value of 1 adds MCS 8 for a total support of MCS 0 through 8, and the value of 2 adds MCS 9 for total support of MCS 0 through 9. The value of 3 is reserved. The two-bit field repeats eight times so that the transmitter can specify the maximum MCS supported for each spatial stream.
- Rx and Tx Highest Supported Data Rate (13 bits each)
These 13-bit fields represent the highest total data rate supported, in units of 1 Mbps. For example, a device that supported a maximum speed of 867 Mbps (80 MHz channels with two spatial streams) would set this field to 0001101100011, which is 867 in binary notation. This field has the length of 13 bits because 13 bits allows representation of up to 8,191 Mbps, which is beyond the maximum data rate in 802.11ac.
Tip
Because the MCS map field only allows three options (MCS 0 through 7, MCS 0 through 8, and MCS 0 through 9), it is not possible to disable low data rates in an 11ac network.
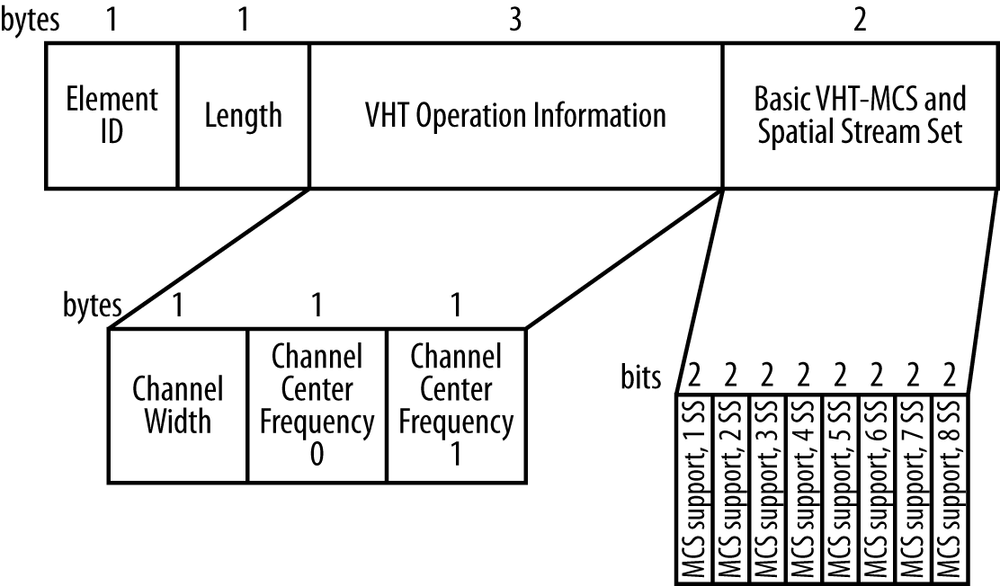
The VHT Operation Information element
All 802.11 physical layers have an information element (IE) that describes their operation, and the VHT PHY is no exception. The VHT Operation IE, shown in Figure 3-4, describes the channel information and the basic rates supported by the transmitter. Basic rates are those rates that are supported by all clients attached to an AP, and therefore are safe to use for frames that are destined for a group of multiple stations. Rate support, which is found in the second field of the IE, is transmitted identically to the rate support in the VHT Capabilities IE. The first part of the information element describes the channels used by the transmitter through the following fields:
- Channel Width (1 byte)
For either 20 MHz or 40 MHz operation, the Channel Width field is set to 0. 80 MHz operation sets this value to 1. Because it is necessary to distinguish the 160 MHz channel width (a value of 2) from the 80+80 MHz channel structure (a value of 3), they receive separate values. All other values of this field are reserved.
- Channel Center Frequency 0 (1 byte)
This fields are used only with 80 and 160 MHz operation, to transmit the center channel frequency of the BSS. In 80+80 MHz operation, it is the center channel frequency of the lower frequency segment.
- Channel Center Frequency 1 (1 byte)
This field is used only with 80+80 MHz operation, and is used to transmit the center channel frequency of the second segment.
Other management frame changes
In addition to communicating capabilities and operating status, some other minor changes were made to management frames and management protocols in 802.11ac:
The Transmit Power Envelope element enables APs to communicate transmission power limits for each of the available channel bandwidths.
The Channel Switch Wrapper element extends the existing channel-switch announcements by enabling a channel switch announcement frame to not only direct devices to a new channel, but also state the channel bandwidth.
The Extended BSS Load element enables an AP to describe the amount of time spent transmitting on each channel bandwidth so that a receiver can see how much time is spent on 20, 40, 80, and 160 MHz operations.
The Operating Mode Notification element describes the current channel width and number of spatial streams active.
Medium Access Procedures
In keeping with its evolutionary nature, 802.11ac does not introduce significant new changes to the way that devices access the network medium. However, with new channel bandwidths come new rules for determining whether the channel is clear. To make the most efficient use of spectrum, 802.11ac also adds new rules for allowing devices to indicate their intended bandwidth consumption in RTS/CTS exchanges.
Clear-Channel Assessment (CCA)
802.11 has always been a “listen-before-talk” protocol in which gaps in the transmission medium usage are an important component of the coordination process that divides up access to the medium among many stations. An important component of the 802.11ac standard is the way that a BSSID can switch channel bandwidth dynamically on a frame-by-frame basis. In any given collection of devices, it is easy to see how some might be line-powered devices without power-saving requirements and demanding the highest possible throughput, while others are battery-operated devices where battery life is at a premium. Rather than enforcing a one-bandwidth-fits-all approach, 802.11ac allows channel bandwidth to be determined on a frame-by-frame basis.
Note
By selecting the channel bandwidth to be used on a per-frame basis, 802.11ac can more efficiently use the available spectrum. When a wide channel is available, high data rates are possible. When only a narrow channel is available, 802.11ac can fall back to lower rates.
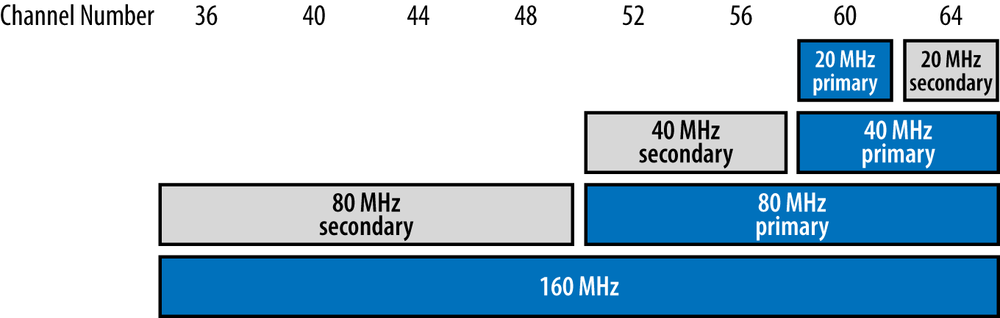
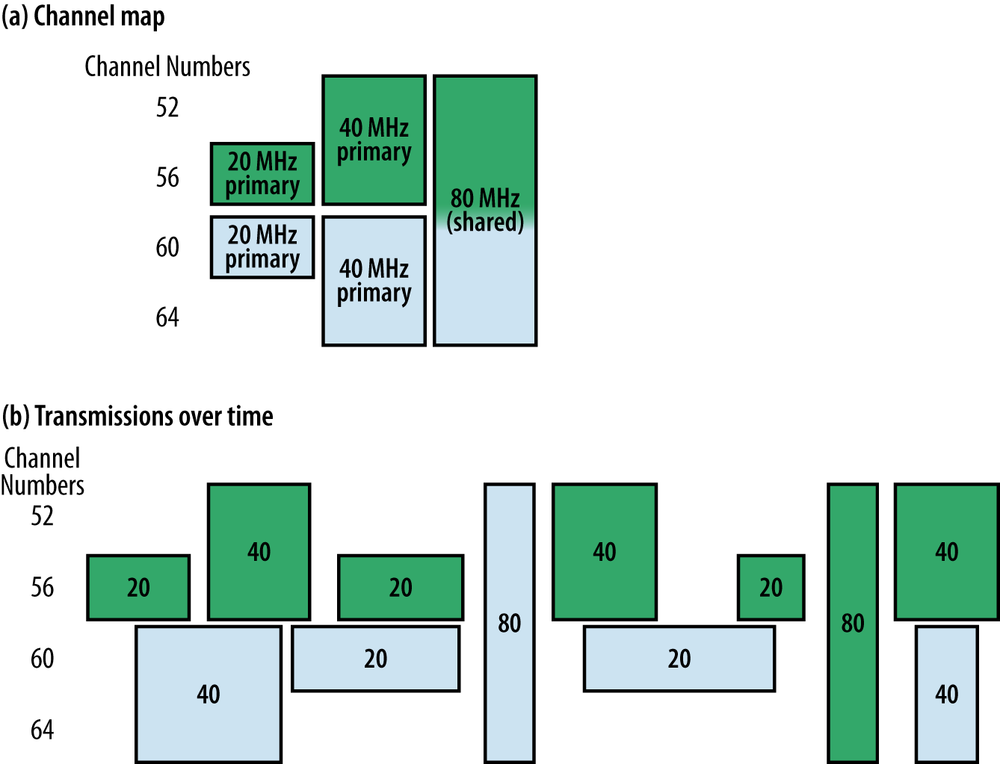
To help with dividing up airtime between channels, 802.11ac introduces the terminology of primary and secondary (or, more formally, non-primary) channels. The primary channel is the channel used to transmit something at its native bandwidth. Figure 3-5 is an illustration of the concept in the lowest eight available channels. For each channel bandwidth, there is one primary channel, meaning that it is the channel used to transmit frames at that channel width. This network will transmit 20 MHz frames on channel 60. To transmit a 40 MHz frame on its 40 MHz primary channel, both channels 60 and 64 must be free. To transmit an 80 MHz frame, the four channels 52 through 64 must all be free. Finally, to transmit a 160 MHz frame, all eight channels from 36 through 64 must be free. Table 3-2 shows the primary and secondary channels for each bandwidth. In practice, 802.11ac can share spectrum much more efficiently than 802.11n because detection of networks on non-primary channels is significantly better with 802.11ac hardware.
| Channel bandwidth | Primary channel | Secondary channel | Total number of 20 MHz channels |
| 20 MHz | 60 | 64 | One (60) |
| 40 MHz | 60 | 52 | Two (60, 64) |
| 80 MHz | 52 | 36 | Four (52, 56, 60, and 64) |
| 160 MHz | 36 | n/a | Eight (36, 40, 44, 48, 52, 56, 60, and 64) |
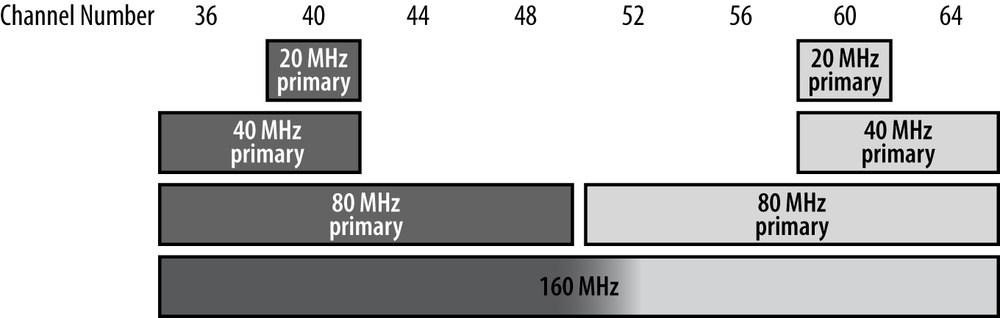
One of the reasons for the notion of primary and secondary channels is that it helps multiple networks to share the same frequency space. Due to the wide variety of devices and data rates in use, a network that is designed for peak speed using 160 MHz channels will not always need the full capacity of the channel. Two networks, such as those shown in Figure 3-6, may share the same 160 MHz channel. They may both transmit 80 MHz frames at the same time because their primary 80 MHz channels are different.
The ability to share wider channels as shown in Figure 3-6 depends on the ability of an 802.11ac device to detect transmissions not only on its primary channel but also on any secondary channels in use. 802.11n’s clear-channel assessment (CCA) capabilities on secondary channels were limited, and thus deploying two 802.11n networks that overlapped required in practice that the primary channels be identical. 802.11ac has sufficiently good secondary-channel CCA capabilities that two networks can readily be deployed without overlap, leading to gains for the whole network because a much larger fraction of transmissions can be done in parallel. This single subtlety in the specification allows for a wide range of deployment options for 802.11ac networks.
Basic channel access rules
The most basic channel access rule is that a frame can be transmitted if the medium is idle. Whether the medium is idle depends on how wide a channel the transmission is using. Once the relevant channel has been determined to be idle, a VHT device may:
Transmit a 20 MHz frame on its primary 20 MHz channel. Clear-channel assessment looks only at the primary 20 MHz channel.
Transmit a 40 MHz frame on its primary 40 MHz channel. Naturally, this requires that the secondary 20 MHz channel is also idle and has passed the CCA check.
Transmit an 80 MHz frame on its primary 80 MHz channel. As you might expect at this point, this requires that both the primary 40 MHz channel and the secondary 40 MHz channel are idle.
Transmit a 160 MHz frame on the 160 MHz channel, but only if both the primary and secondary 80 MHz channels are idle.
If any of the necessary channels are not idle, the device must report that the channel is busy and use the backoff procedure to reacquire the channel. With the backoff procedure, the transmitter will wait until the medium is idle, allow the distributed interframe space (DIFS) to elapse, and then attempt retransmission. As part of the retransmission, the device will select a random number to use as the slot number within the contention window. In most cases, the “winner” of a retransmission attempt during contention will be the station that selects the lowest backoff number.[26]
Sensitivity requirements
To report that the channel is busy, 802.11 has two methods: signal detection and energy detection. Signal detection requires that a receiver find, lock onto, and begin decoding an 802.11-compatible signal. The second method, energy detection, looks only at the raw energy received in the band: if it is sufficiently high, the channel is reported as busy. 802.11ac keeps the same rules for CCA sensitivity for 20 MHz and 40 MHz channels that were first adopted in 802.11n, and adds rules for the new wider channels. Table 3-3 summarizes both the signal thresholds and the energy thresholds for primary and secondary channels. Two rules guide the development of these thresholds. First, every time the channel bandwidth doubles, the required signal threshold also doubles (+3 dB is a doubling of power). Second, the rule for energy detection is that on a non-primary channel, energy of 20 dB over the minimum sensitivity indicates that a channel will be busy because that is likely to be sufficient power to have an intelligible signal over the background noise.
Protection and Coexistence of 802.11ac with Older 802.11 Devices
For the designers of 802.11ac, ensuring compatibility with existing 802.11 equipment was a key requirement to meet in developing the new specification. But because of the evolutionary nature of the VHT PHY, no new protection mechanisms are required. Reuse of the OFDM PHY’s physical layer header ensures that any 5 GHz device will be able to detect VHT transmissions and identify that the medium is busy.
The introduction of 802.11ac expands the compatibility matrix in the 5 GHz band from two concurrently operating technologies to three, and the compatibility considerations in a broadcast network medium extend not only to intended receivers but to any receiver. Table 3-4 describes the compatibility between transmitters of frames and their intended receivers. That is, if a transmitter of the type in the left column sends a frame directed to a receiver of the type in any of the other three columns, what will the result be? One of the major methods used to support coexistence is backward compatibility. When built, 802.11ac devices will also incorporate 802.11a and 802.11n data rates, and thus will be able to send to older peers at older data rates.
| Transmitter type | 802.11a receiver | 802.11n receiver | 802.11ac receiver |
| 802.11a | Designed operation | 802.11n devices may receive 802.11a frames | 802.11ac devices may receive 802.11a frames |
| 802.11n | 802.11n device transmits 802.11a frames (backward compatibility) | Designed operation | 802.11ac devices may receive 802.11n frames |
| 802.11ac | 802.11ac device transmits 802.11a frames (backward compatibility) | 802.11ac device transmits 802.11n frames (backward compatibility) | Designed operation |
The more interesting side of coexistence is that any device may listen to a frame. If two 802.11ac devices are communicating with each other, how can those frames be constructed so that an older 802.11a-only device is not harmed and may still participate in sharing the network medium? By adopting the OFDM preamble, it is possible for an 802.11ac frame to be sent into the radio network and for an 802.11a device to listen to that frame’s preamble, calculate the duration for which the medium will be busy, and defer transmitting to avoid collisions. Table 3-5 summarizes how various device types listening to transmissions from each of the 5 GHz PHYs will react.
| Transmitter type | 802.11a listener | 802.11n listener | 802.11ac listener |
| 802.11a | Designed operation | 802.11n devices listen to 802.11a frames and defer medium access to avoid collisions | 802.11ac devices listen to 802.11a frames and defer medium access to avoid collisions |
| 802.11n | 802.11n greenfield frames require RTS/CTS or CTS-to-self protection; 802.11n mixed-mode frames require no special protection | Designed operation | 802.11ac devices listen to 802.11n frames and defer medium access to avoid collisions |
| 802.11ac | 802.11ac uses a compatible physical preamble, allowing 802.11a devices to read the medium as busy and avoid collisions | 802.11ac uses a compatible preamble, allowing 802.11n devices to read the medium as busy and avoid collisions | Designed operation |
Dynamic Bandwidth Operation (RTS/CTS)
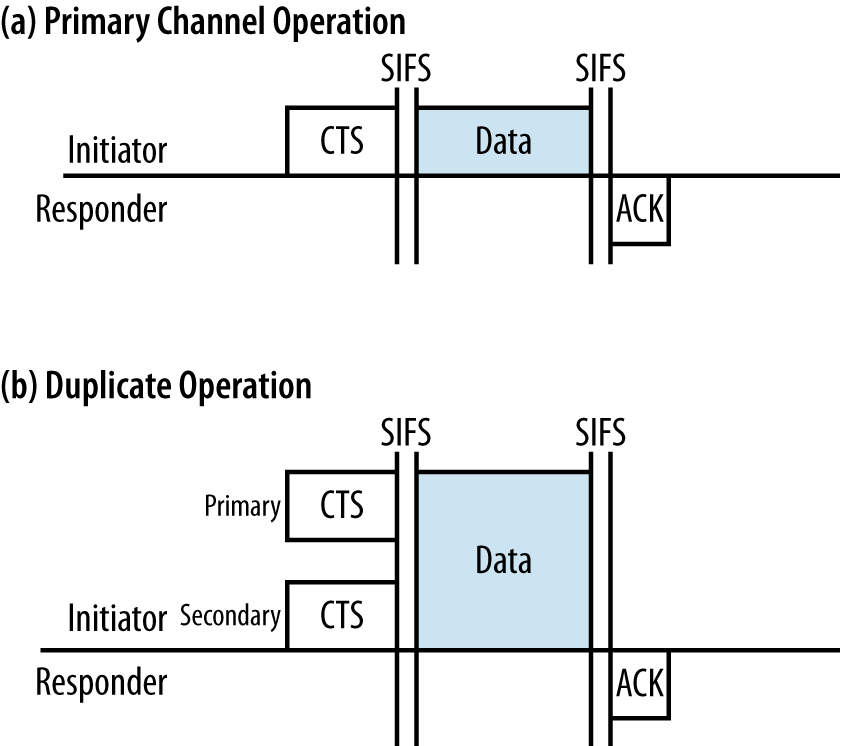
From its inception, 802.11 defined the Request to Send/Clear to Send (RTS/CTS) exchange to deal with hidden nodes. The CTS frame was later reused to provide management of the medium when transmitting to older stations. RTS and CTS frames are used only to manage access to the network medium, and they work in part because they may be transmitted at lower rates so that they may be received and understood by all stations.[27] In Figure 3-7(a), the initiator of the CTS exchange transmits the CTS at 802.11a rates, which may be understood by all recipients. All receivers of that CTS frame then know to defer access to the medium for the duration requested in the CTS, even if they are not able to receive and decode the data frame.
To manage access to a wider channel, a type of transmission called a non-HT duplicate frame is used, which is exactly what it sounds like. Breaking it down etymologically, there are two attributes that go into non-HT duplicate transmission. First, the frame is transmitted using non-HT methods, which, practically speaking, means 802.11a transmission. Second, the frame is duplicated across multiple channels. Figure 3-7(b) shows the duplication occurring across a primary and secondary channel for a 40 MHz transmission. Wider channels may require three (80 MHz) or even seven (160 MHz) duplicate frames.
Duplicate frames are used to create dynamic bandwidth signaling in 802.11ac. Even if a network is occupying, say, 80 MHz of spectrum, it will send Beacon frames and carry out access control on its primary channel. It may interact with older 802.11a stations on its primary 20 MHz channel and 802.11n stations on its primary 40 MHz channel, and only occasionally transmit frames using the full 80 MHz bandwidth. For much of the time, a network will not need its full bandwidth. Therefore, 802.11ac extended the RTS and CTS to add bandwidth signaling. Normally, an RTS or CTS frame only works to clear the channel on which it is transmitted. When it is used in duplicate mode to clear out multiple channels simultaneously, this is indicated by setting the Individual/Group bit in the transmitter address to 1, and the address is called a bandwidth signaling transmitter address.
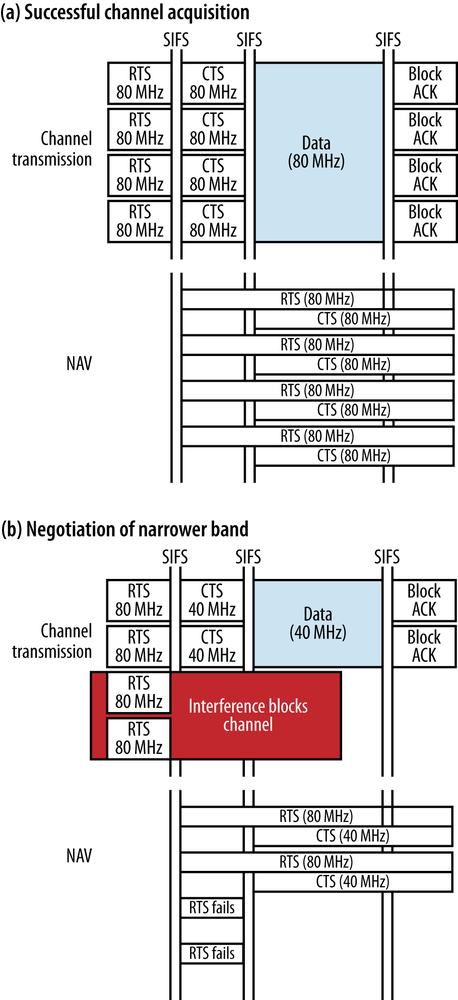
Figure 3-8 shows how the RTS and CTS work together to negotiate the bandwidth. The initiator of a frame transmission has a frame to transmit, and would like to transmit that frame over the full 80 MHz shown in the diagram. To acquire the channel, it sends a duplicated RTS frame across all four 20 MHz channels, indicating that it would like to acquire the whole channel. In Figure 3-8(a), the receiver performs a clear-channel assessment, finds that the entire 80 MHz channel is free, and sends a CTS indicating so. As a result of the exchange, the NAV, shown in the bottom of the picture, is set on all four channels so that any other networks will defer transmission.
Figure 3-8(b) shows the dynamic bandwidth process at work. Just as in the previous scenario, the initiator begins by sending a duplicated RTS to all four 20 MHz channels in the desired 80 MHz channel. However, due to interference at the responder (say, from a colocated AP that has already taken control of two channels), it is not possible to send a CTS indicating the entire 80 MHz channel is free. Therefore, the responder sends a CTS frame on the two free channels, acquiring 40 MHz of spectrum for the transmission. With the RTS/CTS exchange complete, the initiator can send its frame using a 40 MHz transmission. Although it is a reduced channel bandwidth, the two 802.11ac devices have found and negotiated the maximum bandwidth available for transmission.
Multiple networks can use dynamic bandwidth to share access to the same wide channels. Figure 3-9(a) shows a channel map for two 802.11ac networks with primary 20 MHz channels of 56 and 60, respectively. They do not share their primary 20 MHz or 40 MHz channels, but they must share the same 80 MHz channel for transmission. If these were the only two networks installed in the same area, they could transmit 20 MHz or 40 MHz frames independently, but each would have to wait for a time when the other network was idle before using an 80 MHz channel. Figure 3-9(b) shows an example of how the network might be used over time.
For 20 MHz and 40 MHz operation, the networks operate as independent neighbors; it is only when 80 MHz transmissions are required that the dynamic bandwidth aspect of the network comes into play. This feature in 802.11ac allows two networks to share a high-capacity 80 MHz channel without contention most of the time, which is valuable because many devices will either not be capable of 80 or 160 MHz operation, or will disable it to save battery power.
Security
With the adoption of the 802.11i amendment in 2004, the 802.11 working group set out the core tenets of the Robust Security Network (RSN). In particular, the Counter Mode with CBC-MAC Protocol (CCMP) has proven to be a durable cryptographic system, and has successfully protected data on wireless networks from its standardization through the adoption of 802.11n in 2009. As part of the 802.11n specification, earlier and weaker cryptographic systems were removed from use.[28] 802.11ac makes no major changes to security. CCMP remains the primary method used to protect data frames as they fly through the air at 802.11ac data rates.
At its heart, CCMP uses the Advanced Encryption Standard (AES) cipher. Knowing the cipher used is only part of the story, though, because encryption algorithms can be used in many different ways, called modes. Roughly speaking, a cipher mode describes how much data is encrypted in an application of the cipher and how multiple cipher blocks can be linked together to protect larger amounts of data, such as a LAN frame or TCP segment. From a security perspective, CCMP remains strong. Cryptographic systems, however, may need to be replaced for reasons other than security; of the many other reasons that may lead to the replacement of a cryptographic system, insufficient performance is common.[29]
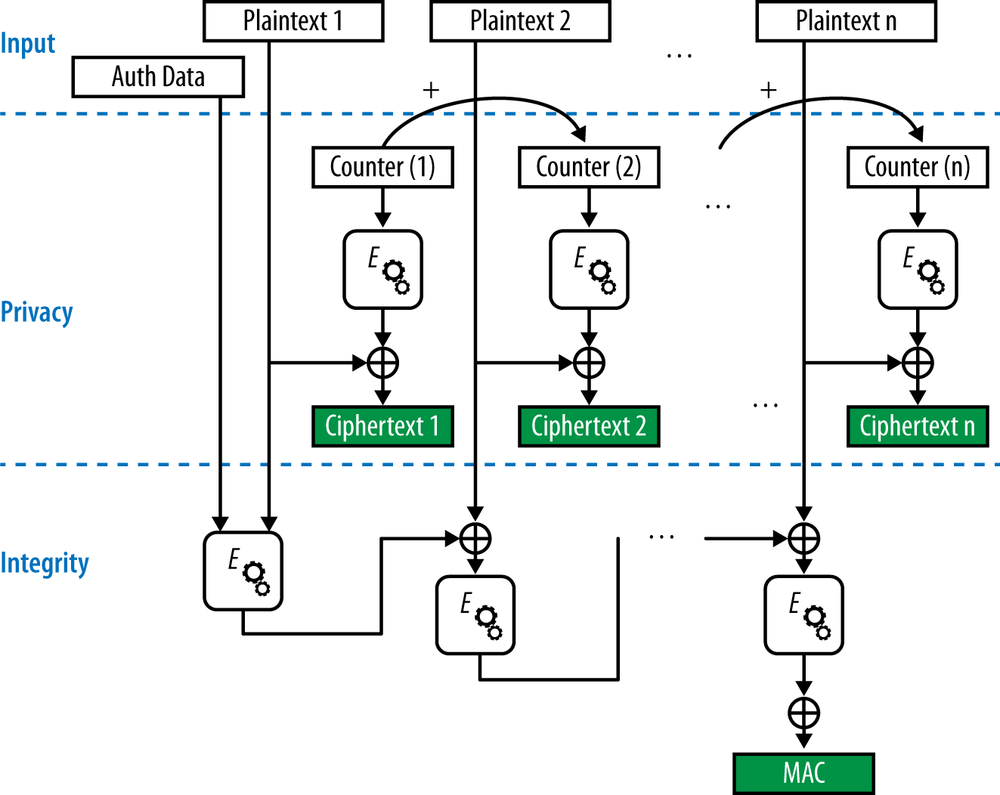
CCMP uses AES in the counter mode (the first C in CCMP) and then applies a cipher-block chained message authentication code (CBC-MAC, the second C and the M in CCMP). Figure 3-10 shows how the system works. AES blocks are 128 bits long. To handle frames ranging in size from the shortest ARP frame to a maximum-length aggregate frame, the frames are first divided into blocks. Each block is authenticated and encrypted, with the authentication requiring one AES operation and the encryption requiring a second AES operation. Authentication uses cipher-block chaining; the “chaining” in the name refers to the way that the output from the first block is used on the second block, the output from the second block is used on the third block, and so on. Message authentication of each block depends on the previous block’s operations being completed, preventing parallel operations. To encrypt, say, a standard 1,500-byte Ethernet frame requires about 200 AES operations.
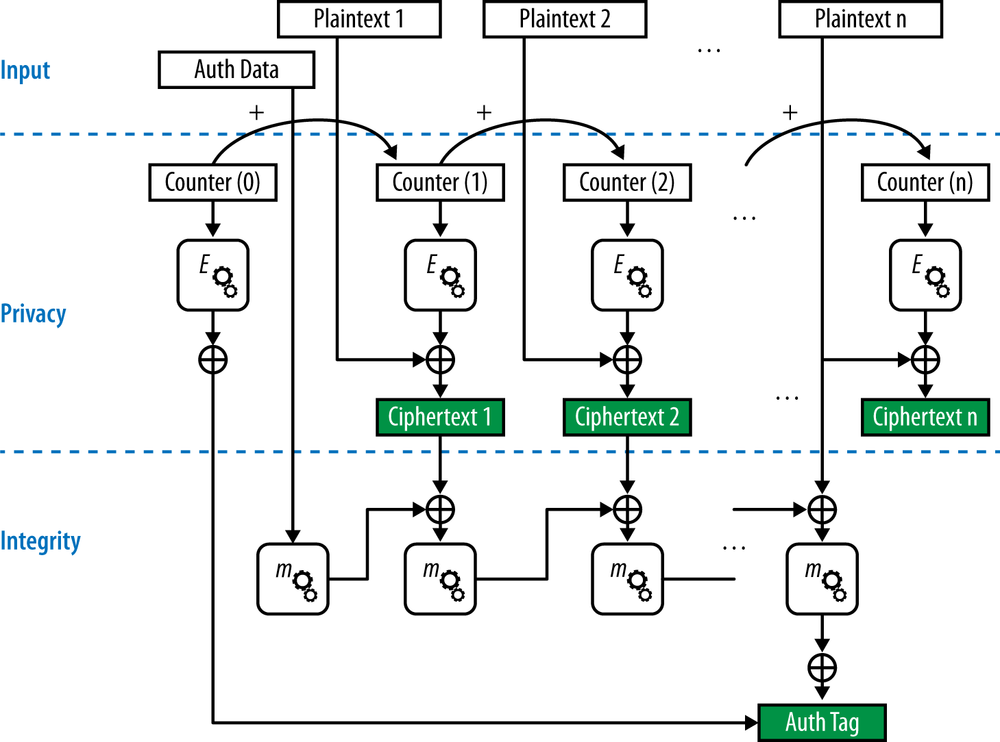
Although CCMP has no theoretical limit to the speeds it can operate at, the use of a block-chaining mode for authenticating each block cannot be parallelized, so there is a practical performance limit placed on real-world implementations. Due to concerns about high latency in 802.11ad, that project specified the Galois/Counter Mode Protocol (GCMP). At a high level, GCMP is functionally similar to CCMP. A large data set, such as a wireless LAN frame, is given to the encryption layer for protection. The frame is divided into blocks, and those blocks are authenticated and encrypted. Figure 3-11 shows the system block diagram. While it looks similar, there is one important difference between the two in the authentication step. Rather than using block chaining to authenticate each data block, GCM uses a Galois field multiplication. In contrast to block chains that require each block to be processed before moving on to the next one, Galois field multiplications can be run in parallel. In addition, Galois multiplications are less computationally intensive than the cipher block encryption algorithms required by a CBC-MAC.[30] By transferring the work of authenticating the frame from the block cipher to the Galois field, GCMP also reduces the number of encryption algorithms, further increasing efficiency.
GCM is not widely used within 802.11 wireless LANs.[31] The GCM-based cryptosystem being standardized by 802.11ad (GCMP) is not required for use with 802.11ac, but it may be used if it is present. The additional performance of GCMP will not be needed to introduce early 802.11ac products, but as speeds increase and multi-user MIMO drives up the total data rate, the efficiency of GCMP may be required. When GCMP is used in 802.11ac, it must be used for both the unicast and broadcast/multicast frames.
Mandatory MAC Features
Although 802.11ac is a complex specification, the MAC changes are comparatively simple. Table 3-6 classifies protocol features as either mandatory or optional; this chapter has concentrated on the main mandatory features.
| Feature | Mandatory/Optional | Comments |
| A-MPDU (receive and transmit) | Mandatory | A-MPDU operation was widely implemented in 802.11n hardware, and it is required for use with all 802.11ac devices |
| Single-user beamforming | Optional | Discussed in Chapter 4 |
| Multi-user beamforming | Optional | Discussed in Chapter 4 |
| CCA on secondary channels | Mandatory | |
| Bandwidth signaling in RTS/CTS | Mandatory to receive, optional to transmit | |
| GCMP | Optional | Unlikely to be required by industry certification programs |
[21] For the format of the HT-variant HT Control field, see Figure 5-1 in 802.11n: A Survival Guide.
[22] 802.11ac does not add any new aggregation methods; for an introduction to the use of aggregation in 802.11, see Chapter 5 of 802.11n: A Survival Guide.
[23] Describing 4.5 MB of data requires 23 bits of information in the header. Practically speaking, putting that information in the VHT Signal header would require expanding it to be two OFDM symbols, which would add 4 μs to each frame. By putting timing information in the VHT Signal header and moving the byte field into the high-rate modulated data field, the efficiency of the network is increased.
[24] 802.11n allowed values from 0 to 3, which capped the maximum A-MPDU at 64 KB.
[25] STBC spreads a single spatial stream across two transmit chains and two space-time streams. Therefore, an eight-stream-capable device can transmit a maximum of four spatial streams when STBC is used.
[26] For more information on the channel acquisition procedure, see Chapter 3 of 802.11 Wireless Networks: The Definitive Guide.
[27] For more information on how the RTS and CTS frames use the network allocation vector to manage medium access, see 802.11 Wireless Networks: The Definitive Guide, Chapters 4 and 14. The former chapter describes framing details and how the network allocation vector works; the latter chapter contains a detailed discussion of 802.11g protection.
[28] TKIP and WEP cannot be used with 802.11n data rates. This prohibition extends to 802.11ac data rates because all 802.11ac devices are required to implement 802.11n protocol features. For more discussion on reasons for removing TKIP and WEP support with 802.11n, see Chapter 5 of 802.11n: A Survival Guide.
[29] For example, Triple DES is widely believed to be practically secure, but its slow speed is a serious drawback.
[30] Both Intel and AMD now include instructions for Galois field multiplication in microprocessors. The Carry-less Multiplication (CLMUL) instruction set on Intel’s Westmere, Sandy Bridge, and Ivy Bridge chips and AMD’s Bulldozer and Piledriver can be applied to perform the Galois field multiplication. An Intel application note specifically describes how to use these instructions for support of GCM: http://software.intel.com/en-us/articles/intel-carry-less-multiplication-instruction-and-its-usage-for-computing-the-gcm-mode/.
[31] It is, however, a common element in LAN cryptosystems. RFC 4106 describes how to apply GCM within the IPsec framework, and it was adopted by 802.1AE-2006 (“MACsec”) due to its superior efficiency.
Get 802.11ac: A Survival Guide now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.