CHAPTER 19Interacting with Threat Actors
This final chapter details why it usually pays off to roll up your sleeves and jump in the muck with the threat actors you are investigating. You will be incredibly surprised (as I was) at how much information they will unknowingly give up.
Drawing Them Out of the Shadows
I had just returned home from the final DerbyCon, where I had given a talk on “Hunting Cyber Criminals.” I was on my way to taking my daughter to soccer practice when I received an overly suspicious tweet.
I knew my talk at DerbyCon would catch the attention of certain people, which is why I specifically included The Dark Overlord in the talk description, and made sure to include their name in my promotional tweets.
To take it one step further, I intentionally asked Adrian Crenshaw (and DerbyCon) to not publish the video of the talk for this exact reason. I had a suspicion that people close to the groups would catch wind of my talk and want to hear what was said.
The plan worked. A few days after my talk, I received the following tweet from a mysterious figure known as YoungBugsThug (Figure 19.1).
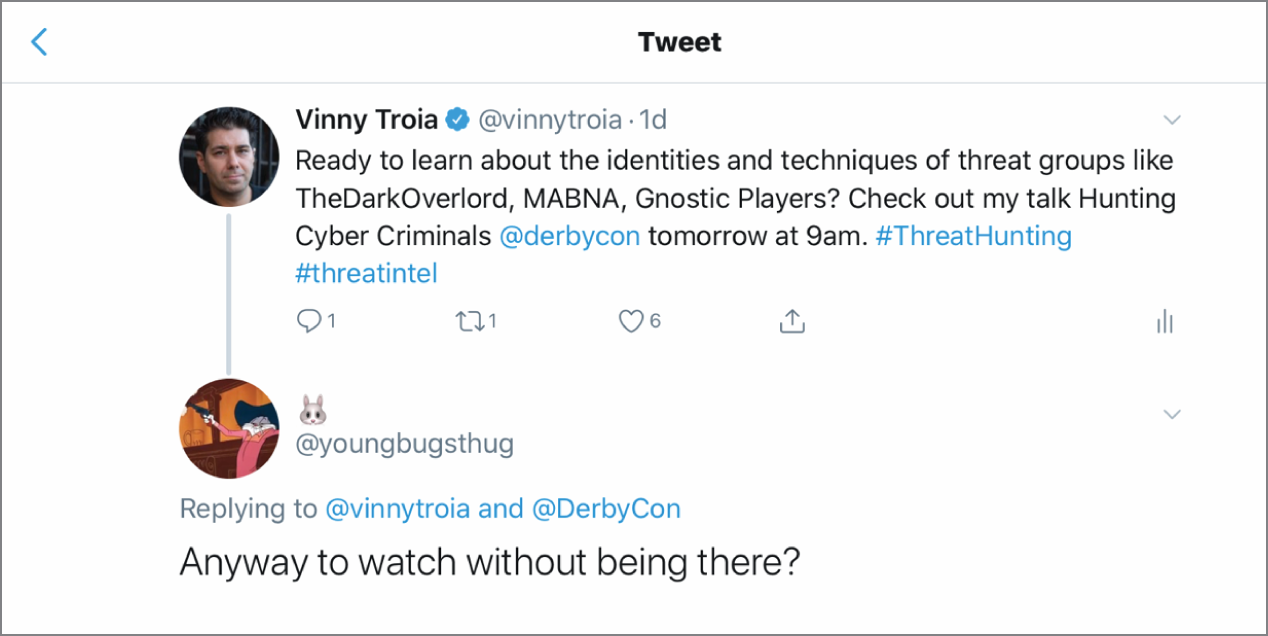
Sure, this could have been anyone. But then I received the following private message on Twitter from the same user (Figure 19.2).
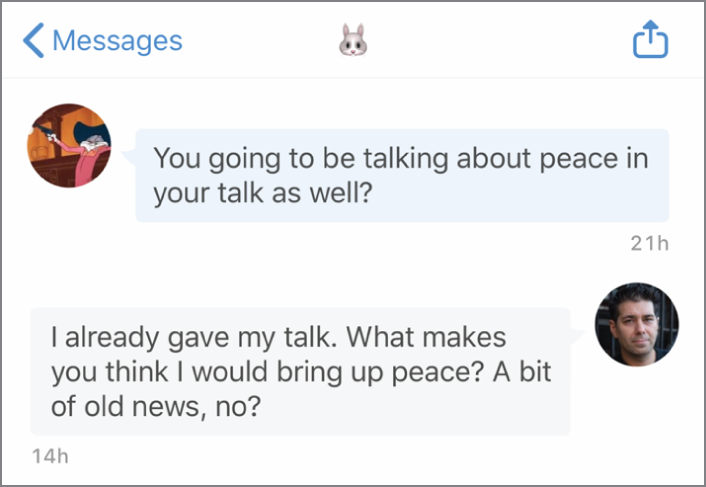
Why would someone ...
Get Hunting Cyber Criminals now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

