Chapter 7. Data Transmission Security
In Chapter 2, we discussed at length the protection of identification and account security through the use of proper hashing and salting techniques. Even though account security is vitally important to any system, what about security for any data that is being transmitted from one party to another, as that data might be sensitive in nature or contain privileged user information?
In this chapter, we explore numerous data-security techniques that are designed to protect data in motion, or better said, data that is moving between parties. We’ll look at a few of these techniques in depth:
-
SSL secure data transmission
-
Asymmetric key cryptography, better known as public/private key encryption
-
Symmetric key encryption, better known as shared secret encryption
Let’s start out by exploring our ideal secure scenario.
SSL/TLS
In an ideal scenario, when working with data security as web developers, Secure Sockets Layer (SSL) is the mechanism that you should be targeting as your data security standard for a user. If you’re not familiar with how it works, you’ll be familiar with seeing the effect of an SSL certificate being used on websites that you visit, Figure 7-1, for example shows the expanded certificate information for https://www.google.com.
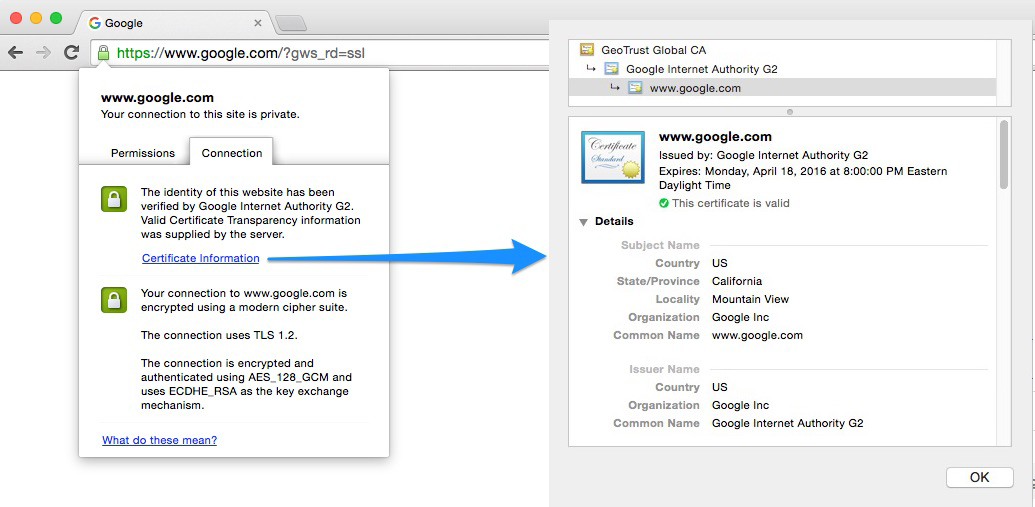
Figure 7-1. SSL certificate on Google
SSL, and its successor, Transport Layer ...
Get Identity and Data Security for Web Development now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

