Chapter 1. Introduction
But I think the real tension lies in the relationship between what you might call the pursuer and his quarry, whether it’s the writer or the spy.
John le Carré
Once relegated to the secretive realms of national security and military operations, intelligence has become something that is fundamental to the daily functioning of many organizations around the world. At its core, intelligence seeks to give decision makers the information that they need to make the right choice in any given situation.
Previously, decision makers experienced significant uncertainty because they did not have enough information to make the right decisions. Today they are likely to feel there is too much information, but just as much ambiguity and uncertainty as in the past. This is especially the case with network security, where there are fewer traditional indications that a significant action is actually about to take place. To make decisions about how to prepare for and respond to a network security incident, decision makers need analysts who understand intelligence fundamentals, the nuance of network intrusions, and how to combine the two into an accurate assessment of a situation and what it means for their entire organization. In short, they need analysts who can conduct intelligence-driven incident response.
Before diving into the application of intelligence-driven incident response, it is important to understand the evolution of cybersecurity incidents and their responses, and why it is so relevant in this field. This chapter covers the basics of cyber threat intelligence, including its history, recent activity, and the way forward, and sets the stage for the concepts discussed in the rest of this book.
Intelligence as Part of Incident Response
As long as there has been conflict, there have been those who watched, analyzed, and reported observations about the enemy. Wars have been won and lost based on an ability to understand the way the enemy thinks and operates, to comprehend their motivations and identify their tactics, and to make decisions—large and small—based on this understanding. Regardless of the type of conflict, whether a war between nations or a stealthy intrusion against a sensitive network, intelligence guides both sides. The side that masters the art and science of intelligence—analyzing information about the intent, capability, and opportunities of adversaries—and is able to act on that information will almost always be the side that wins.
History of Cyber Threat Intelligence
One of the best ways to understand the role of intelligence in incident response is by studying the history of the field. Each of the events discussed in the following paragraphs could (and often do!) fill entire books. From the iconic book The Cuckoo’s Egg by Cliff Stoll (Pocket Books) to recent revelations about decades-old intrusions, such as Moonlight Maze, the history of cyber threat intelligence is intriguing and engaging and offers many lessons for those working in the field today.
The first intrusion
In 1986, Cliff Stoll was a PhD student managing the computer lab at Lawrence Berkeley National Laboratory in California when he noticed a billing discrepancy in the amount of 75 cents, indicating that someone was using the laboratory’s computer systems without paying for it. Our modern-day network security–focused brains see this and scream, “Unauthorized access!” but in 1986 few administrators would have jumped to that conclusion. Network intrusions were not something that made the daily news, with claims of millions or even billions of dollars stolen; most computers connected to the internet belonged to government and research institutes, not casual users, and it was easy to assume everyone using the system was friendly. The network defense staple tcpdump was a year from being started. Common network discovery tools such as Nmap would not be created for another decade, and exploitation frameworks such as Metasploit would not appear for another 15 years. The discrepancy Stoll noticed was more easily expected to be a software bug or bookkeeping error, as it seemed that someone had simply not paid for their time.
Except that it wasn’t. As Stoll would discover, he was not dealing with a computer glitch or a cheap mooch of a user. He was stalking a “wily hacker” who was using the Berkeley lab’s network as a jumping-off point to gain access to sensitive government computers, such as those used by the White Sands Missile Range and the National Security Agency (NSA). Stoll monitored incoming network traffic, printing reams of paper to keep a record, and began to profile the intruder responsible for the first documented case of cyberespionage. He learned the typical hours the attacker was active, monitored the commands he ran to move through the interconnected networks, and observed other patterns of activity. He discovered how the attacker was able to gain access to the Berkeley lab’s network in the first place by exploiting a vulnerability in the movemail function in GNU Emacs, a tactic that Stoll likened to a cuckoo bird leaving its egg in another bird’s nest to hatch and inspiring the name of his book on the intrusion, The Cuckoo’s Egg.
Understanding the attacker meant that it was possible to protect the network from further exploitation, identify where he may target next, and allow a response—both on the micro level (identifying the individual carrying out the attacks) and on the macro level (realizing that nations were employing new tactics in their traditional intelligence-gathering arsenal and changing policies to respond to this change). Sharing this understanding was key to protecting Lawrence Berkeley National Lab and many other government organizations as well.
Destructive attacks
In 1988, Cornell University student Robert T. Morris hacked into a computer lab at the Massachusetts Institute of Technology (MIT) and released a computer program that was designed to replicate itself to as many computers as possible without being detected. It did this by exploiting a backdoor in the internet’s email delivery system as well as a flaw in the “finger” program that identified network users. It may have just been a harmless experiment—or a prank, as some have described it—that few people ever knew about, but it did not work exactly as Morris intended and became part of cybersecurity history (which is just like regular history, but cooler). Morris’s cyber “worm” ended up crashing 6,000 computers, which was about 10% of the internet of the time, with systems at Harvard, Princeton, Stanford, Johns Hopkins, NASA, and the Lawrence Livermore National Laboratory among the many victims. Investigators from the FBI were struggling to inspect the activity, unsure if it was an outage or an attack, when Morris called two friends and admitted that he was the one behind the worm. One of the friends called the New York Times, which led to the eventual identification and conviction of Morris for violations of the new Computer Fraud and Abuse Act of 1986 (CFAA).
Although there was no nefarious intent behind this worm—it was really just another example of how programs don’t always behave exactly the way that their creator intended them to—there were far-reaching implications that can still be seen today. As the internet became more and more critical to operations, it became even more important to be able to quickly identify and remediate other intrusions or destructive attacks. The Computer Emergency Response Team (CERT) was established in 1998 at Carnegie Mellon University as a professional, trained response team responsible for providing assessments and solutions for cyberattacks. Morris’s worm also highlights why it is important to be able to quickly attribute an attack. In 1988 there had been significant “warming” of the Cold War, with Reagan and Gorbachev meeting in Moscow and Soviet troops beginning to withdraw from Afghanistan. If this worm had inaccurately been blamed on Soviet activity—which was actually the case for the activity from The Cuckoo’s Egg—it could have significantly changed the course of history.
Moonlight Maze
In the decade following The Cuckoo’s Egg and Morris’s worm, the field of incident response improved, not just with the creation of CERT, but because of the professionalization of the field itself across the government, military, and private sectors. In addition, the emergence of proper network monitoring tools meant that defenders weren’t reliant on printers scattered around a basement to identify malicious network activity. This increase in capabilities was fortuitous, as intrusions not only continued but grew in scope and sophistication. In 1998, the US government identified what is believed to still be the largest and longest-running intrusion into government networks—codenamed Moonlight Maze.
In March 1998, the US government noticed anomalous activity within several sensitive and restricted networks, including the Pentagon, NASA (yes, NASA has apparently always been a target for intrusions), and the Department of Energy (DOE). Further analysis identified the same malicious activity at several universities and revealed that the activity had been ongoing for at least two years. The sustained nature of this activity was unlike any of the previous intrusions (as far as was known at the time), which had seemed more targeted and short-lived. Unlike those instances, the adversaries had left strategic backdoors in different parts of the network so that they could return at will. Information was being gathered from numerous locations that often seemed unrelated.
We have been fortunate enough to work closely with people who directly investigated and responded to Moonlight Maze, both in the 1990s and today, as there are still many unknowns and many insights to be gained from this intrusion. Talking with these individuals and reading through the numerous reports on the intrusion hammers home the point that intelligence work is critical to incident response and that cyber threat intelligence bridges the gap between what is happening on the strategic level with national interests and foreign adversaries and how those adversarial goals and actions show up on a computer network. By 1998, the US had a full-scope intelligence community actively looking and listening for signs of foreign interference, but the largest network attack went unnoticed until it was detected “by accident” because intelligence work had not yet been fully modified to account for actions taken against a network.
Moonlight Maze kicked cyber threat intelligence capabilities into the modern era. Computer networks were not something that might be impacted from time to time; these networks were now being targeted directly for the information and access they held. Computer networks were part of intelligence collection, and intelligence needed to play a role in their defense.
Modern Cyber Threat Intelligence
Over the decades, cyber threats have grown and morphed. Adversaries are not just foreign governments or curious students. Organized criminals, identity thieves, scammers, ideologically motivated activists, and others have realized the impact that their activities could have when directed at digital targets instead of physical ones. These adversaries use an ever-expanding set of tools and tactics to attack their victims and actively attempt to evade detection. At the same time, our reliance on our networks has increased, making incidents even more impactful. Understanding the attacker has gotten much more complicated and much more important.
Understanding how to identify attacker activity and how to use that information to protect networks are the fundamental concepts behind a more recent addition to the incident responder’s toolkit: cyber threat intelligence. Threat intelligence is the analysis of adversaries—their capabilities, motivations, and goals. Cyber threat intelligence (sometimes abbreviated as CTI) is the analysis of how adversaries use the cyber domain to accomplish their goals. See how these levels of intelligence play into one another in Figure 1-1.
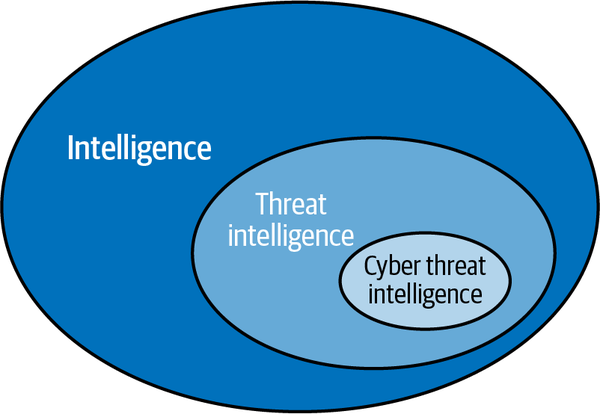
Figure 1-1. From intelligence to cyber threat intelligence
Initially, intelligence analysts came into the picture after an intrusion like Moonlight Maze to understand what the overall intrusion told us about the adversary. What were their goals, their motivations, their capabilities? What was their organizational structure? These were all things that were important for a strategic understanding and long-term planning, but not things that would immediately provide value to those trying to defend their networks from the attacks of today, tomorrow, or sometimes even last week. Cyber threat intelligence began to focus more on tactical and technical details that were more immediately actionable, learning along the way what types of information were most valuable in different situations. Cyber threat intelligence analysts didn’t just bring data; they also brought insights.
In information security, we traditionally focus on observable concepts; we like things that are testable and reproducible. Cyber threat intelligence, meanwhile, lives in the area between observations and interpretation. We may not know for sure that an adversary will attempt to access employee financial records, but we can conduct analysis on data about past intrusions and successful attackers outside of our network and make recommendations for the systems and types of data that may need additional protection. Not only do we need to be able to interpret information, but we also need to be able to convey it in a way that is meaningful to the intended audience to help them make decisions. Looking back on his historic analysis of the intrusions in The Cuckoo’s Egg, Stoll identified “the need for a story” as one of his key takeaways from the entire experience. “I thought I could just show people the data and they would understand,” he said. “But I was wrong. You need to tell a story” (SANS CTI Summit 2017).
The Way Forward
New technologies give us more information about the actions that attackers take as well as additional ways to act on that information. However, we have found that with each new technology or concept implemented, the adversary adapted; worms and viruses with an alphabet soup of names changed faster than our appliances could identify them, and sophisticated, well-funded attackers were often more organized and motivated than many network defenders. Ad hoc and intuitive intelligence work would no longer suffice to keep defenders ahead of the threat. Analysis would need to evolve as well and become formal and structured. The scope would have to expand, and the goals would have to become more ambitious.
In addition to detecting threats against an organization’s often nebulous and ephemeral perimeter, analysts would need to look deeper within their networks for the attacks that got through the lines, down to individual user systems and servers themselves, as well as look outward into third-party services to better understand the attackers who may be targeting them. The information would need to be analyzed and its implications understood, and then action would have to be taken to better prevent, detect, and eradicate threats. The actions taken to better understand adversaries would need to become part of a formal process and a critical part of information security operations: threat intelligence.
Incident Response as a Part of Intelligence
Intelligence is often defined as data that has been refined and analyzed to enable stakeholders to make better decisions. Intelligence, therefore, requires data. In intelligence-driven incident response, there are multiple ways to gather intelligence that can be analyzed and used to support incident response. However, it is important to note that incident response will also generate cyber threat intelligence. The traditional intelligence cycle—which we cover in depth in Chapter 2—involves direction, collection, processing, analysis, dissemination, and feedback. Intelligence-driven incident response involves all of these components and helps inform direction, collection, and analysis in other applications of threat intelligence as well, such as network defense, secure software development, and user awareness training. Intelligence-driven incident response doesn’t end when the intrusion is understood and remediated; it generates information that will continue to feed the intelligence cycle.
Analysis of an intrusion, no matter if it was successful or failed, can provide a variety of information that can be used to better understand the overall threat to an environment. The root cause of the intrusion and the initial access vector can be analyzed to inform an organization of weaknesses in network defenses or of policies that attackers may be abusing. The malware that is identified on a system can help expose the tactics that attackers are using to evade traditional security measures such as antivirus or host-based intrusion-detection tools and the capabilities they have available to them. The way an attacker moves laterally through a network can be analyzed, and that intelligence can be used to create new ways to monitor for attacker activity in the network. The final actions that an attacker performed (such as stealing information or changing how systems function), whether they were successful or not, can help analysts understand the enemy’s motivations and goals, which can be used to guide overall security efforts. There is essentially no part of an incident-response engagement that cannot be used to better understand the threats facing an organization and improve future defense and response.
For this reason, the various processes and cycles outlined in this book are aimed at ensuring that intelligence-driven incident response supports overall intelligence operations. Although they provide specific guidance for utilizing cyber threat intelligence in incident response, keep in mind that wider applications can be used as intelligence capabilities expand.
What Is Intelligence-Driven Incident Response?
Cyber threat intelligence isn’t a new concept, simply a new name for an old approach: applying a structured analytical process to understand an attack and the adversary behind it. The application of threat intelligence to network security is more recent, but the basics haven’t changed. Cyber threat intelligence involves applying intelligence processes and concepts—some of the oldest concepts that exist—and making them a part of the overall information security process. Threat intelligence has many applications, but one of the fundamental ways it can be utilized is as an integral part of the intrusion-detection and incident-response process. We call this intelligence-driven incident response and think it is something every security team can do, with or without a major capital investment. It’s less about tools, although they certainly help sometimes, and more about a shift in the way we approach the incident-response process. Intelligence-driven incident response will help not only to identify, understand, and eradicate threats within a network, but also to strengthen the entire information security process to improve those responses in the future.
Why Intelligence-Driven Incident Response?
Over the past few decades, our world has become increasingly interconnected, both literally and figuratively, allowing attackers to carry out complex campaigns and intrusions against multiple organizations with the same effort that it used to take to target a single entity. We are long past the point where we can automatically assume that an intrusion is an isolated incident—in fact, while we used to be stunned to find overlaps and connections between intrusions, now we are suspicious when we don’t see overlap. When we better understand the adversary, we can more easily pick up on the patterns that show commonalities between intrusions. Intelligence-driven incident response ensures that we are gathering, analyzing, and sharing intelligence in a way that will help us identify and respond to these patterns more quickly.
Operation SMN
A good example of intelligence-driven incident response is the analysis of the Axiom Group, which was identified and released as a part of a Coordinated Malware Eradication (CME) campaign in 2014 called Operation SMN.
For more than six years, a group of attackers known as the Axiom Group stealthily targeted, infiltrated, and stole information from Fortune 500 companies, journalists, nongovernmental organizations, and a variety of other organizations. The group used sophisticated tools, and the attackers went to great lengths to maintain and expand access within the victims’ networks. As malware was detected and the incident-response process began within various victim organizations, coordinated research on one of the malware families used by this group revealed that the issue was far more complex than originally thought. As more industry partners became involved and exchanged information, patterns began to emerge that showed not just malware behavior, but the behaviors of a threat actor group working with clear guidance. Strategic intelligence was identified, including regions and industries targeted.
This was an excellent example of the intelligence cycle at work in an incident-response scenario. Not only was information collected, processed, and analyzed, but it was disseminated in such a way as to generate new requirements and feedback, starting the process over again until the analysts had reached a solid conclusion and could act with decisiveness, eradicating 43,000 malware installations at the time that the report was published. The published report, also part of the dissemination phase, allowed incident responders to better understand the tactics and motivations of this actor group.
SolarWinds
In December 2020, news broke of a massive intrusion at the Texas-based company SolarWinds, which makes software for monitoring and managing IT networks and is a very popular tool in many large networks, including cybersecurity companies, governments, and Fortune 500 companies. The activity was detected after the cybersecurity firm FireEye, a SolarWinds customer, identified that their networks had been compromised and a set of tools they developed for identifying intrusions had been accessed by an unknown entity. Their own investigation into the intrusion on their network led them to identify SolarWinds as the source of the intrusion.
Their analysis indicated that the SolarWinds networks had been compromised in late 2019 and their software tampered with, in that a software update that was pushed to all its clients contained a backdoor that would allow the adversaries access to those networks as well. This was not the first software-based supply chain attack; however, it was notable for its size and scale—estimates suggested that more than 18,000 SolarWinds customers were impacted. It was also notable for its response, which, 20 years after Moonlight Maze, showed how far cyber threat intelligence has come as a discipline. Once identified, FireEye published a blog post with details about the incident and ways for others to detect activity on their network. Additional teams jumped in to analyze activity on their networks and continued to share indicators and findings, both publicly and through established threat-sharing groups, allowing a picture of the overall attack to quickly develop. The Department of Homeland Security published guidance on supply chain attacks, taking the response from a mentality of just reacting to one isolated incident to thinking about how this new information shapes the way the industry should think about preparing for intrusions in the future. While certainly not a perfect process, the SolarWinds compromise illustrates the role that cyber threat intelligence can play in incident response and how it not only can help the organizations directly impacted but also can help to surface important lessons for others.
Both the Axiom Group attacks and the SolarWinds software supply chain intrusion were information-seeking, espionage-related attacks, but nation-state-sponsored attackers aren’t the only thing that incident responders have to worry about. Financially motivated criminal activity is also evolving, and those actors are also working hard to stay ahead of defenders and incident responders. One of the most significant tactical changes for financially motivated criminals in recent years is the move to ransomware. Ransomware attacks use tools to encrypt data on a network and then charge a ransom for the key to decrypt the data. The concept of ransomware has been around for decades; however, its usage has increased drastically since 2012, along with its impact. Although ransomware attacks do not always involve strategic and coordinated attacks against multiple organizations, the groups executing ransomware attacks often target different victims using the same tactics, the same toolsets, and often the same targeting information. Defenders working against these financially motivated attacks can also leverage intelligence-driven incident response to identify early indications that their networks have been breached by these actors before the actual encryption process has begun.
Conclusion
Despite the many advances in the computer security field, attackers continue to adapt—but they do not have to outpace defenders. Intelligence-driven incident response allows us to learn from attackers; to identify their motivations, processes, and behaviors; and to identify their activities even as they seek to outwit our defenses and detection methods. The more we know about attackers, the better we can prevent, detect, and respond to their actions.
We have reached the point where a structured and repeatable process for implementing intelligence in the incident-response process is necessary, and this book aims to provide insight into that process. Throughout this book, we provide various models and methods that can be viewed as the building blocks of intelligence-driven incident response. We discuss why these models are beneficial and how they integrate with incident response. There is no one-size-fits-all approach. In many cases, the incident or the organization will dictate which specific combination of models and approaches fits best. Understanding the foundational principles of intelligence and incident response, as well as the specific methods for integrating them, will allow you to develop and build a process for intelligence-driven incident response that will work for you and the needs of your organization.
Get Intelligence-Driven Incident Response, 2nd Edition now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

