June 2016
Beginner to intermediate
322 pages
6h 18m
English
Next, let's perform some live analysis on the infected machine in hand. This live analysis will give us quick results. It may overwrite some traces in the system, but in our case here, we have already acquired our evidence.
Listing the running processes will allow us to notice any maliciously-named processes that may relate to malware behavior. We can list the running processes using the native tasklist command:
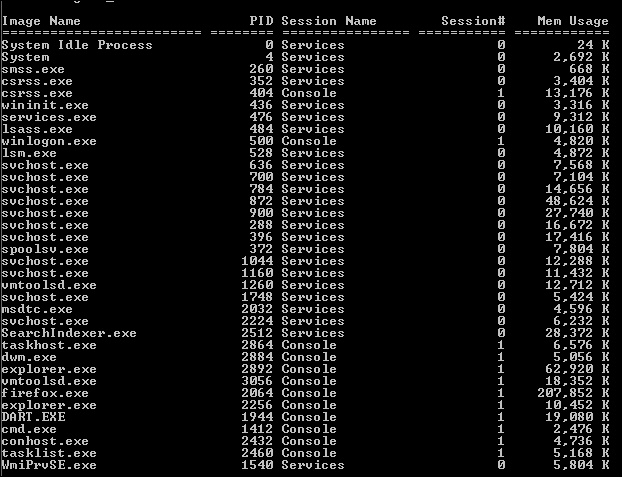
We can also use processexplorer from Sysinternals. We will notice no malicious names, but we can see that there are two processes named explorer.exe within the system. One holds an ID of 2256 ran for compatibility ...