A Network Diagram
Figure 11-1 shows connections from the Internet to the central office to a large office, a small office, and a remote user. It is important to note the flow of traffic throughout the VPN. PPTP servers validate incoming traffic. This encrypted traffic passes through interposing firewalls and is relayed directly to the PPTP server. The traffic is then routed to the desired internal network node. The Cisco PIX firewall, on the other hand, immediately directs authorized traffic to the network and thus provides a faster backbone for the VPN.
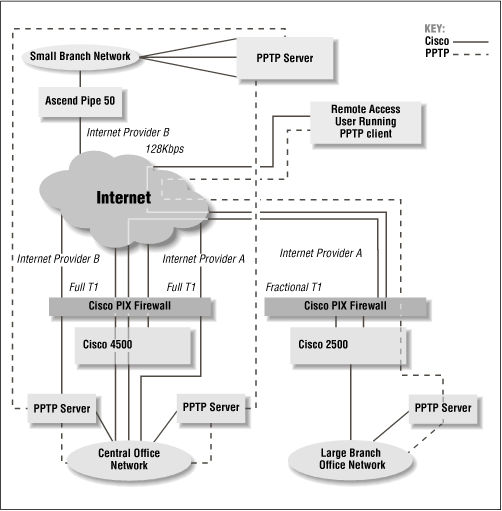
Figure 11-1. VPN hardware, software, and protocols
Regardless of the need or resources available, if your enterprise requires secure network connections over the Internet, there is a solution available. Other solutions, such as IPSec, L2F, SSH, or L2TP, would work just as efficiently. What should be noted is that your organization’s needs should result in the VPN network solution chosen.
Get Virtual Private Networks, Second Edition now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

