Chapter 1. A Model of Virtualization
Model of Virtualization
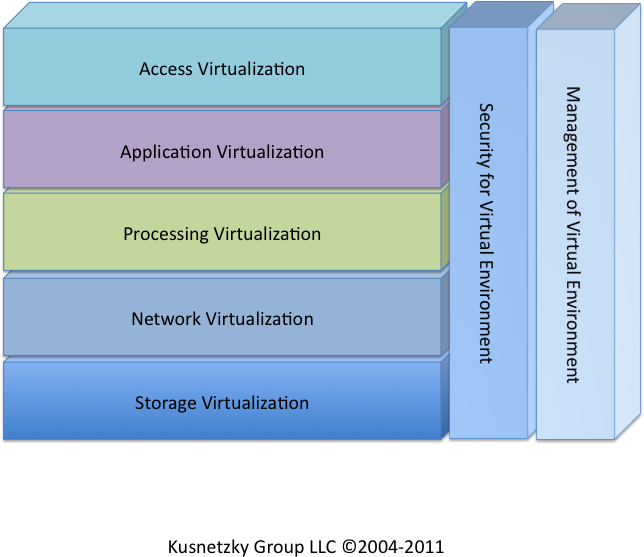
Analysts often find that it is much easier to understand a complex environment if they build a reference model. The Kusnetzky Group Model of virtualization (Figure 1-1) is an example. Reference models must be comprehensive and the segments must be mutually exclusive to be really useful.
Over time, most of the functions that computers perform have in some way benefited from virtualization. It is important to note that some products incorporate features that straddle one or more layers of the model. Those products are typically assigned to the layer describing their most commonly used functions. As one would expect, industry and technological changes require that the model be revisited regularly to determine if previous categories should be merged into a single new category or deleted.
What Is Virtualization?
Virtualization is a way to abstract applications and their underlying components away from the hardware supporting them and present a logical or virtual view of these resources. This logical view may be strikingly different from the physical view. The goal of virtualization is usually one of the following: higher levels of performance, scalability, reliability/availability, agility, or to create a unified security and management domain.
This virtual view is constructed using excess processing power, memory, storage, or network bandwidth.
Virtualization can create the artificial view that many computers are a single computing resource or that a single machine is really many individual computers. It can make a single large storage resource appear to be many smaller ones or make many smaller storage devices appear to be a single device.
Layers of Virtualization at Work
There are many layers of technology that virtualize some portion of a computing environment. Let’s look at each of them in turn.
- Access virtualization
Hardware and software technology that allows nearly any device to access any application without either having to know too much about the other. The application sees a device it’s used to working with. The device sees an application it knows how to display. In some cases, special-purpose hardware is used on each side of the network connection to increase performance, allow many users to share a single client system, or allow a single individual to see multiple displays.
See Chapter 2 for more information.
- Application virtualization
Software technology allowing applications to run on many different operating systems and hardware platforms. This usually means that the application has been written to use an application framework. It also means that applications running on the same system that do not use this framework do not get the benefits of application virtualization. More advanced forms of this technology offer the ability to restart an application in case of a failure, start another instance of an application if the application is not meeting service-level objectives, or provide workload balancing among multiple instances of an application to achieve high levels of scalability. Some really sophisticated approaches to application virtualization can do this magical feat without requiring that the application be re-architected or rewritten using a special application framework.
See Chapter 3 for more information.
- Processing virtualization
Hardware and software technology that hides physical hardware configuration from system services, operating systems, or applications. This type of virtualization technology can make one system appear to be many or many systems appear to be a single computing resource, to achieve goals ranging from raw performance, high levels of scalability, reliability/availability, agility, or consolidation of multiple environments into a single system.
See Chapter 4 for more information.
- Network virtualization
Hardware and software technology that presents a view of the network that differs from the physical view. A personal computer, for example, may be allowed to “see” only systems it is allowed to access. Another common use is making multiple network links appear to be a single link. This approach makes it possible for the link to present higher levels of performance and reliability.
See Chapter 5 for more information.
- Storage virtualization
Hardware and software technology that hides where storage systems are and what type of device is actually storing applications and data. This technology allows many systems to share the same storage devices without knowing that others are also accessing them. This technology also makes it possible to take a snapshot of a live system so that it can be backed up without hindering online or transactional applications.
See Chapter 6 for more information.
- Security for virtual environments
Software technology that controls access to various elements in a virtual environment and prevents unauthorized or malicious use.
See Chapter 7 for more information.
- Management for virtual environments
Software technology that makes it possible for multiple systems to be provisioned and managed as if they were a single computing resource.
See Chapter 8 for more information.
Each of these layers of virtualization will be examined in the following chapters.
Goals of Virtualization
Organizations are often seeking different things when using virtualization technology. An organization’s virtualization goals might include the following:
Allowing any network-enabled device to access any network-accessible application over any network, even if that application was never designed to work with that type of device
Isolation of one workload or application from another to enhance security or manageability of the environment
Isolation of an application from the operating system, allowing an application to continue to function even though it was designed for a different version of the operating system
Isolation of an application from the operating system, allowing an application to function on a foreign operating system
Increasing the number of people that an application can support, by allowing multiple instances to run on different machines simultaneously
Decreasing the time it takes for an application to run, by segmenting either the data or the application itself and spreading the work over many systems
Optimizing the use of a single system, allowing it to work harder and more intelligently (that is, reducing the amount of time the processor sits idle)
Increasing the reliability or availability of an application or workload through redundancy (if any single component fails, this virtualization technology either moves the application to a surviving system or restarts a function on a surviving system)
The organization’s choice of virtualization technology is dependent upon what it’s trying to accomplish. While there are typically many ways to accomplish these goals, some goals direct organizations’ decision-makers to select specific tools.
Get Virtualization: A Manager's Guide now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.