Chapter 12Security Procedures
In this chapter, we review the security techniques that protect LTE against attacks from intruders. The most important issue is network access security, which protects the mobile's communications with the network across the air interface. In the first part of this chapter, we cover the architecture of network access security, the procedures that establish secure communications between the network and mobile, and the security techniques that are subsequently used. The system must also secure certain types of communication within the radio access network and the evolved packet core. This issue is known as network domain security and is the subject of the second part.
The 3GPP security procedures are covered by the 33 series specifications: those for LTE are summarized in TS 33.401 [1]. As in the last chapter, the details of the individual messages are in the specifications for the relevant signalling protocols [2–5]. For a detailed account of security in LTE, see Reference [6].
12.1 Network Access Security
12.1.1 Security Architecture
Network access security (Figure 12.1) protects the mobile's communications with the network across the air interface, which is the most vulnerable part of the system. It does this using four main techniques.
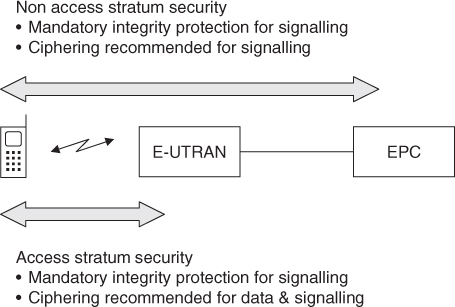
Figure 12.1 Network access security architecture
During authentication, the network and mobile confirm each ...
Get An Introduction to LTE: LTE, LTE-Advanced, SAE, VoLTE and 4G Mobile Communications, 2nd Edition now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

