Chapter 15. Asymmetric Encryption
In the previous chapter, we discussed symmetric encryption and the support available in the .NET Framework. The word “symmetric” is an appropriate description because both Alice and Bob must know the secret key used to encrypt data in order to read it, leading to the problem of agreeing on the key in such a way that Eve is unable to eavesdrop. In this chapter, we discuss an alternative approach to message confidentiality known as “asymmetric encryption.” We’ll explain what it is, how it works, and how it overcomes the problem of exchanging secret keys.
Asymmetric Encryption Explained
Asymmetric encryption, often called "public key” encryption, allows Alice to send Bob an encrypted message without a shared secret key; there is a secret key, but only Bob knows what it is, and he does not share it with anyone, including Alice. Figure 15-1 provides an overview of this asymmetric encryption, which works as follows:
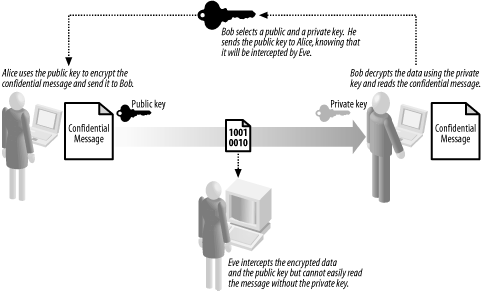 |
Bob creates a pair of keys, one of which he keeps secret and one of which he sends to Alice.
Alice composes a confidential message and encrypts it using the key that Bob has sent to her.
Alice sends the encrypted data to Bob.
Bob uses his secret key to decrypt the data and reads the confidential message.
The key that Bob sends to Alice is the public key, and ...