Chapter 6. IP Network Scanning
Upon identifying IP address blocks of interest, active scanning is undertaken to map the network, catalog accessible hosts, and identify exposed services. The following tactics are covered in this chapter:
-
Use of Nmap to perform initial network scanning
-
Low-level assessment to understand the network configuration
-
Use of Nmap and Metasploit to perform light vulnerability scanning
-
Bulk vulnerability scanning (using Nessus, Qualys, and others)
-
Evasion of intrusion detection and prevention mechanisms
Manual testing is then undertaken to investigate vulnerabilities, exploit known flaws, and launch brute-force password grinding attacks. For reference, Figure 6-1 demonstrates the relationship between IP protocols covered in this chapter.
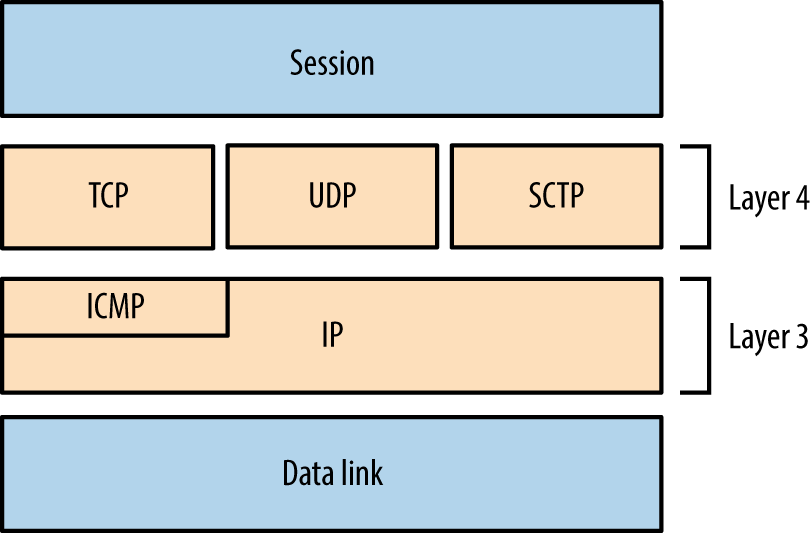
Figure 6-1. Network protocols and respective OSI layers
Initial Network Scanning with Nmap
Available for platforms including Apple OS X, Microsoft Windows, and Linux, Nmap supports IPv4 and IPv6 network scanning via ICMP, TCP, UDP, and SCTP. Now let’s see how to use Nmap to scan an environment.
ICMP
Nmap supports ICMP scanning over both IPv4 and IPv6 to map subnets within larger IP blocks and elicit responses from hosts (depending on configuration). Here are two particularly useful ICMPv4 message types:
- Type 8 (echo request)
- Used by ping and other utilities to identify accessible hosts.
- Type 13 (timestamp ...
Get Network Security Assessment, 3rd Edition now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

