Chapter 4. Protect Your Phone
Hacks 22–25: Introduction
In the mobile information age, mobile phones not only store sensitive information about us, but also act as an identity provider for us when we use mobile network services. Therefore, it is important that we keep our phones physically secure.
It is also important that we keep our phones secure from viruses and other forms of attack. As mobile phones and related services become increasingly sophisticated, many potential security problems can arise because phones are networked in so many ways. In this chapter, you will learn how to secure your device against malicious programs, service theft, and data theft.
Avoid Malicious Software
Protect your Nokia phone against mobile phone viruses, malware, Trojan horses, Bluetooth scanners, and other malicious programs.
As a powerful and connected computing device, the Nokia smartphone suffers the same vulnerability as other connected computers—viruses and other malicious programs can attack them over the network. Those programs can potentially harm the device, leak sensitive information, cause data loss, or even result in big service charges for you. Compared with regular computer viruses, a mobile phone virus can be especially harmful, since it can spread in peer-to-peer local networks; worse, most phone users are not prepared to deal with such viruses.
Basics of Malicious Programs
Before you can act to protect yourself, you need to know a little about how malicious programs can attack your mobile phone. The following is a list of representative malicious programs on smartphones and the harm they cause:
- Force the phone to perform operations that interfere with regular user operations
The original Cabir virus (http://www.sarc.com/avcenter/venc/data/epoc.cabir.html) forces your phone to scan the Bluetooth network all the time, quickly draining the battery.
- Disable some device functionality
The Dampig virus (http://www.sarc.com/avcenter/venc/data/symbos.dampig.a.html) replaces some key system libraries and makes many applications, including the Bluetooth user interface (UI), useless on your phone. The Locknut virus (http://www.sarc.com/avcenter/venc/data/symbos.locknut.html) can cripple your phone to the point that you cannot make voice calls. The Fontal.A virus (http://www.sarc.com/avcenter/venc/data/symbos.fontal.a.html) does not cause immediate problems for your phone, but it does secretly replace several key font files, which prevents the phone from booting up once you reboot it. Bluetooth scanners can send malformed Bluetooth messages to your phone and crash its Bluetooth program, forcing you to reboot your phone to recover.
- Make phone calls or send Short Message Service (SMS) messages to expensive caller-paid services
The Mosquitos Trojan (http://www.sarc.com/avcenter/venc/data/trojan.mos.html) sends messages to premium SMS service numbers without your knowledge or approval. The message costs are billed directly to your service account. Some Bluetooth-based exploits allow a Bluetooth scanner running on a nearby device to remotely dial your phone or make arbitrary connections using AT commands.
- Leak out sensitive personal information
Malicious Bluetooth scanners can allow a cracker to remotely steal the entire memory contents of your phone from another nearby device without your knowledge. In theory, it is also easy to develop a mobile Trojan that gathers information about your contacts, calendar, and media Gallery, and then sends the information to a third-party server on the Internet.
Tip
Cabir is the first virus known to target Nokia Series 60 devices. It is largely a proof-of-concept virus. Cabir spreads over Bluetooth and does not contain a payload (the malicious software that does the actual harm). It is benign, except for the fact that it drains your battery with continuous Bluetooth searches. Later variations of the Cabir virus, such as Cabir.b and Lasco, can do real harm to you and your phone.
Based on their attack methods, malicious software on smartphones can be divided into two categories:
Now, let’s discuss those two types of attacks in more detail.
Viruses and Trojans.
Currently, all Nokia mobile phone viruses are written in Symbian C++ and are deployed to devices as Symbian programs. Although in theory Java-based viruses are possible, they are substantially more difficult to develop and deploy, since Java applications must run in the Java Virtual Machine and must conform to strict Java security policies. Since Java applications do not have direct access to your phone’s physical memory or other low-level device-native features, it is less likely that they can breach or circumvent the phone’s security policies. In fact, there is no known Java virus for Nokia phones. Since Java is the only programming platform on Nokia Series 40 devices, there are no known Nokia Series 40 viruses.
Mobile viruses and Trojans must be downloaded into your phone for them to take effect. Viruses and Trojans can spread in three primary ways:
- Trojan download
The malicious program can present itself as a known (or appealing) Symbian program and trick you into downloading and installing it directly. For instance, the Mosquitos Trojan virus poses as a cracked version of the popular Symbian game, Mosquitos, on certain file-sharing networks. A cracked version of a game is a version that’s been illegally modified to remove the registration module, so you can play it for free. The idea is that you’ll run it, thinking you are running a game, but the Trojan virus will activate when you run it. Other examples include the Dampig virus, which pretends to a cracked version of the FSCaller application, and the Skulls virus, which pretends to be a theme manager application. To prevent Trojan viruses, you just need to be careful about the sources of the programs you download. I recommend that you use only legitimate software downloaded from well-known web sites. Beyond the immediate concern of security, it also helps if you don’t try to circumvent copy protection, and instead, support the developers that work hard on software you want to use.
- Bluetooth
Viruses can spread over the local Bluetooth network. An infected device tries to find all Bluetooth devices in its neighborhood, all the time. Once a device is found, the infected device sends the program over to the new device. The recipient is then presented with a message to accept the incoming file and install it. The original Cabir virus spread in this way. If the recipient is not well informed or if the message is deceiving, he might just install the program. For instance, the Gavno virus presents itself as a “software patch,” borrowing a familiar concept from Microsoft Windows to deceive users. Once the program is installed, it can execute itself and then start to search for nearby Bluetooth devices to spread further.
- MMS
A Bluetooth-based mobile virus can infect devices only within a range of several meters. Hence, the virus can travel only as fast as the devices move, which is the speed of airplanes in modern societies. Some newer mobile phone viruses, such as the Commwarrior, can spread over MMS. The virus tries to send itself via MMS to 256 random phone numbers from your Contacts list. This can potentially allow the virus to spread at the speed of telecommunications, which means it can spread across the world in a very short period of time. And what do you do when you receive an MMS from a friend? You open it, of course. This is the same kind of social engineering that permitted so many Microsoft Outlook-based viruses to spread over the years.
Bluetooth scanners.
Bluetooth scanners exploit insecure implementations of the Bluetooth system software on some phone models. Several Nokia phone models are known to be vulnerable (e.g., Nokia 7650, 6310i, etc.). You can get more information, including an updated vulnerable-device list, from http://www.thebunker.net/security/bluetooth.htm.
A Bluetooth scanner has to be physically close to your phone (e.g., in a conference hall or classroom) for Bluetooth to work. There are three known types of Bluetooth attacks:
- Bluesnarf
This type of attack can be launched from untrusted (a.k.a. unpaired [Hack #11] ) devices. The attacker can steal information, including your Contacts list, calendar, photos, etc., from your phone.
- Backdoor
This type of attack has to be launched from a previously paired device. The attacker can get access to almost all the functionality on your phone.
- Bluebug
This type of attack involves creating a Bluetooth serial profile [Hack #11] to your phone, and then hijacking the phone’s voice and data connections.
Tip
Bluejacking is often cited as a fourth type of Bluetooth attack. But it is really just a prank. It works as follows. The prankster creates a contact entry on her own phone and enters a prank message into the “name” field. For instance, the “name” of this contact might be “Your phone belongs to us.” Then, the prankster sends the contact to random Bluetooth phones as a business card [Hack #35] . The recipient suddenly sees an unsolicited prank message—“Your phone belongs to us”—on his phone screen.
Preventive Measures
The best protection is prevention: knowing how the malicious programs work. You can take several simple precautions to minimize your risk.
Only install trusted programs.
The key to prevent viruses and Trojans is to be extremely careful about what you install. If you download .sis applications from the Web, you need to verify that they are indeed legal and that they come from an authorized source. If you receive an application over Blue-tooth, as a general rule do not install it unless you already had a conversation with the sender and are expecting it. Do not install any program from email or MMS message attachments.
Minimize Bluetooth exposure.
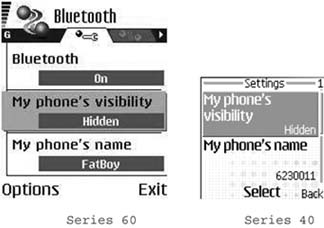
To minimize the risk of Bluetooth-based viruses and Bluetooth scanners, you should turn off Bluetooth in public places. If that is not possible, you can make the device invisible (see Figure 4-1) so that it does not show up when other devices scan the network. If you do receive a Bluetooth message from a friend, talk to her and confirm her intentions before you accept or install the application file.
Use a personal firewall.
Most malicious mobile programs rely on the network to spread or work. You can prevent them by controlling the network connections on your phone. One of the most effective network control tools is a firewall. By installing a firewall on your phone, you can:
Prevent unauthorized Bluetooth or General Packet Radio Service (GPRS) incoming connections and file transfers
Prevent Bluetooth scanners from discovering or pairing with your phone
Prevent Bluetooth scanners from accessing any data or services on your phone
Prevent Trojans from sending out any information from your phone
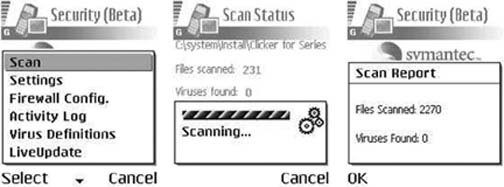
The Symantec Mobile Security for Symbian (currently in beta) provides a personal firewall for Nokia Series 60 phones. You can download it from https://www-secure.symantec.com/public_beta/. Via the firewall, you can specify several different levels of communication constraints. Figure 4-2 shows the mobile phone firewall in action.
Remove the Virus
If you know the name of the virus that infected your device, you can search for it via Google. You can probably find a lot of security bulletins from research sites such as http://www.symantec.com and http://www.f-secure.com. Most of these bulletins include a complete description of the virus, including the files it installs on your device. For instance, the following two URLs point to the F-Secure and Symantec bulletins for the Cabir virus:
With a file browser tool such as FExplorer [Hack #20] , you can follow the instructions to remove the virus from your device.
In practice, it is difficult to know the exact name of a virus. For instance, the Cabir virus has at least eight very similar variations. So, the preceding method is not always practical in the real world. In most cases, a much simpler way to erase the malicious program and reverse the damage is to perform a deep reset. “Reset and Restore Your Phone” [Hack #23] discusses how to reset your phone and then restore its functionality via data backups.
Use Antivirus Software
In the previous two sections, I covered generic approaches to protect your phone and recover from an attack. But those approaches do not always prevent all attacks. Manually resetting the phone is time consuming and does not reverse the financial loss you might have incurred from the virus.
If you are really concerned about mobile viruses, you can invest in antivirus software to protect your phone. Antivirus programs for Symbian-based phones (e.g., the Nokia Series 60 smartphones) are available from the following vendors:
F-Secure Mobile Anti-Virus from http://www.f-secure.com/products/fsmavs60/
SimWorks Anti-Virus from http://www.simworks.biz/sav/
Symantec Mobile Security for Symbian (beta) from https://www-secure.symantec.com/public_beta/
Like antivirus software on computers, mobile antivirus software scans all files on your device to look for specific patterns of known viruses (a.k.a. the virus signature). If it finds one, it isolates the infected file and presents you with the option to remove it. Figure 4-3 shows a full scan performed by the Symantec Mobile Security for Symbian program (beta).
The full device scan takes a long time and consumes a lot of battery power, so don’t perform a full scan on a regular basis. To save time and energy, the antivirus programs support incremental scan modes that check only incoming files, such as files you’ve downloaded or created using software on your phone. After the first full device scan, the antivirus programs run in the background and automatically scan all incoming files from the Web, Bluetooth, MMS, and email messages, and check for virus signatures as they arrive. If they detect an infected program, you will be advised not to install it.
As you would expect, the key for a successful antivirus program is to have a complete list of virus signatures to check against. This is a moving target, since new viruses might be written after the antivirus software is released. So, all mobile antivirus programs come with a subscription service that allows the program to update its virus signature database periodically over the Internet via the phone’s data connection.
Reset and Restore Your Phone
Reset your phone without losing data or custom settings.
As a power user, you often need to fiddle with your phone to try out new software, experiment with new configuration settings, or even clear up viruses or other malicious programs. This fiddling can sometimes cause the phone software to crash, freeze, or otherwise behave abnormally (e.g., it will be unable to connect to the network or unable to run some programs). Some phone viruses discussed in “Avoid Malicious Software” [Hack #22] can also freeze your phone. This is when the reset feature in Nokia phones comes in handy. In this hack, you will learn not only how to reset your phone, but also how to back up and restore data in a systematic manner.
Two Types of Resets
Nokia phones can handle two types of resets: normal reset and deep reset.
Normal reset.
On a Series 40 device, you can do a normal reset via the Settings → Restore factory settings menu. The normal reset simply resets the most basic phone settings, such as the security code, whether to enable speed dialing, the display brightness, and the screensaver time-out, to their factory preset values. It does not alter the applications mapped to the right soft key (i.e., the GoTo key), nor does it alter any of the network connection settings.
On a Series 60 device, you can do a normal reset by entering the service code *#7780# on the phone’s idle screen, as though you are making a phone call. Alternatively, you can use the Tools → Settings → Phone settings → General → Orig. factory settings menu to perform the normal reset.
The Series 60 normal reset does everything the Series 40 normal reset does. In addition, it forces the phone to reload all the .ini files from the Read-Only Memory (ROM) to the C: drive under the Symbian OS. Hence, many application settings are restored. For instance, a normal reset on a Series 60 phone restores the soft-key shortcuts on the idle screen to factory settings, deletes the phone’s Bluetooth name, eliminates all the GPRS access point settings [Hack #10] , and resets data storage options in the Camera or Messaging application to “Phone memory” [Hack #21] . The email Inbox settings [Hack #60] , however, are left untouched.
Tip
The phone prompts you for the current security code before it resets itself. The default security code is 12345.
On both Series 40 and Series 60 phones, the normal reset leaves intact all the user data on the phone, such as contacts, calendar items, wallpapers, images, tones, messages, and third-party applications. While it is a safe operation, the normal reset is of limited value, since most of the time it is the user data that messes up the phone. A much more powerful reset is a deep reset.
Deep reset.
Deep reset is not available on Series 40 phones, since user data and applications on those devices do not have direct access to the operating system, and hence, cannot crash the phone unless it is in bad shape—in which case, you should have it repaired.
Tip
If you need to delete all the contacts or images on a Series 40 phone, you have to do it manually. The Nokia PC Suite [Hack #15] provides a phone content browser that can help you speed up your cleaning procedures.
On a Series 60 device, a deep reset is equivalent to reformatting the C: drive and wiping out all the user data in the phone’s internal flash memory. The data on the MultiMediaCard (MMC) card, however, is not touched. You can reformat the MMC card via the Options → Format mem. card menu in the Extras → Memory menu. You can force a deep reset on a Series 60 device in two ways:
Tip
Although the MMC card should not be reformatted during a deep reset, you should probably take your MMC card out of the phone before doing a deep reset to be on the safe side.
You should see the word formatting on the screen during the deep reset.
Warning
It is very important that the phone has power while it is formatting. Do not take the battery out in the middle of formatting! In fact, I recommend that you connect the phone to an AC adapter before you do a deep reset.
Of course, after a deep reset “fixes” your phone’s problems, you still need to restore some of the user data to make the phone useful again. That is more complex than simply resetting and requires you to plan a backup strategy before you start fiddling with the phone. Backing up and restoring give you the ability to roll the phone back in time to the stable and useable state before your latest failed experiments. In the rest of this hack, I will discuss data backup and restore strategies.
Automatic Backup and Restore
Nokia provides tools to automatically back up and restore the flash memory in your Series 60 phone (i.e., the C: drive). You can do it via a companion PC or via the phone’s MMC card, which is not formatted during a deep reset. Automatic backup is easy to use and is safe in most occasions.
Use the PC Suite.
The Nokia PC Suite [Hack #15] allows you to back up the entire content of the phone’s internal memory (the C: drive) to a PC file. The full backup file includes the following:
Contacts
Calendar items
Images and other media files in the phone’s Gallery
Settings including GPRS access points, email, and other connection settings
Personal preferences such as wallpaper, ring tones, and speed-dial shortcuts
Applications including Symbian C++ and Java programs
I recommend doing the backup periodically. If you mess up and have to do a deep reset, you can locate the closest clean backup file and restore it to the phone via the PC Suite. The PC Suite puts your backup files into %SystemRoot%\Nokia\Phone Model\Backup (e.g., C:\Nokia\Nokia 3650\Backup for a typical backup for a Nokia 3650 phone).
The PC Suite also allows you to back up and restore a subset of data in the flash memory. You can choose any combination of the following four categories of data: contacts, calendar items, documents, and images.
Use the MMC card.
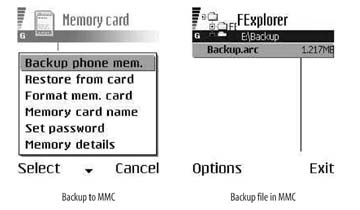
You can back up everything in the phone’s main memory to the MMC card via the Extras → Memory menu. Just choose the Options
→ Backup phone mem. menu and the data is backed up in a file, E:\Backup\Backup.arc, on the MMC card (see Figure 4-4).
When you decide to restore the phone memory from the backup file, just choose the Options → Restore from card menu in the Extras → Memory menu. The phone will reboot itself after the memory contents are restored.
The Backup.arc file is written over every time you perform a backup. So, by default, you can recover to the phone state only at the last backup time. To work around this, you can copy the Backup.arc file off the memory card after each backup and archive it on your computer periodically. If you need to recover to an earlier date, you can copy the correct Backup.arc file back to the memory card and then perform the restore operation.
Manual Backup and Restore
The automatic backup and restore solution is easy and effective. But it requires discipline to back up your data regularly and to remember to back it up before each experiment. It is also less useful if the backup interval is too long and too much user data is changed between backups. In addition, if your phone is infected with a virus before the last backup and you have just noticed the virus now, how do you know which past backup is the clean one that can be safely restored?
Using manual methods described in this section, you will be able to selectively back up some of your phone data right before the deep reset, and then restore it after the reset. Here, I assume that you can still boot up your phone and operate it.
Tip
Even if your phone is fully functional and is not affected by malicious programs, you can still optimize the phone’s memory by "refreshing” it. The manual backup process before refreshing gives you the opportunity to eliminate stale data and programs.
Connection settings.
First, you should back up your current network settings, such as SMS server numbers, email settings [Hack #60] , and GPRS access points [Hack #10] . You can simply go through the phone and write down those settings on a piece of paper for your records. After resetting, you can manually enter those settings back into the phone.
Some versions of the Nokia PC Suite (e.g., the PC Suite for Nokia 3650) provide a utility to back up and restore phone connection settings in a PC file. You can use the utility to automate the connection settings backup process.
PIM data.
The phone’s Personal Information Manager (PIM) data, such as contacts and calendar items, can be synchronized with PIM applications on desktop computers [Hack #36] , [Hack #37] , and [Hack #38] . You can synchronize them back to the phone after the reset.
If synchronization is not an option for you, you can use the backup and restore utility on the Nokia PC Suite, and request that it back up/restore the contacts and calendar data only (see the previous section in this hack).
Or, if you want to pick and choose which PIM items to back up, you can copy them to the PC via the Nokia PC Suite’s phone browser. The PIM items appear as .vcf (for contacts) and .vcs (for calendar items) files on the PC. When you copy them back, the phone automatically converts them to the phone’s internal format.
Documents.
The best way to save documents—such as the email messages, MMS messages, audio/video files, and images—from being erased in a deep reset is to save them in the MMC card, which you can take out of the device when you do the deep reset. You can configure the Messaging and Camera applications to automatically save files to the MMC card. Please see “Manage Your Phone’s Memory” [Hack #21] for more information on this subject.
If you do not save the phone documents in the MMC card, you can still copy and save everything in the phone’s Gallery and Messages folders to a PC via the PC Suite before the deep reset.
Applications.
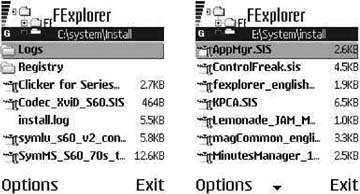
If you have installed your applications on the MMC card, they will still be available on the phone’s Main menu after the deep reset. However, the Application Manager program might not keep track of them anymore. So, you might lose the ability to update or remove those applications. For the Application Manager to work, you need to copy the contents of the C:\System\Install\ directory to the E:\System\Install\ directory on the MMC card. Those directories contain the installers (i.e., the .sis archive file) of applications installed on the device (see Figure 4-5). Since those system directories are not available in the Nokia PC Suite’s phone browser, you have to copy them manually using a program such as FExplorer.
If you did not install applications on the MMC card and you have not backed up the entire phone memory using an automatic backup method covered in the previous section, you must reinstall all the applications from scratch.
Deal with Lost or Stolen Phones
Protect your wallet and privacy by preventing unauthorized access, even when you do not physically possess your phone.
It is easy to lose a mobile phone. Most of us have had the experience of forgetting the phone on our desk or in our car. Our kid might take it to school, or our spouse might take it on a trip. Sometimes, the phone might even get stolen. A lost phone can expose you to big security risks, even if it is out of your physical control for only a couple of minutes:
Someone might be able to obtain the sensitive personal and business information stored on the device.
Someone might use the phone to make expensive calls or send messages to premier SMS service numbers and have the cost billed to you.
In this hack, you will learn how to protect yourself against information theft and unauthorized service access when you lose your phone.
Tip
Remember to remove all locks, security codes, and personal data from your phone before you sell it on eBay! The best way to do this is to perform a hard reset and then format the memory card.
Lock the Phone
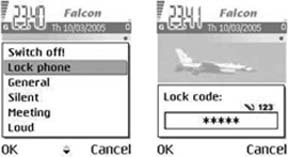
You can lock most Nokia phones (this is much more restrictive than locking the keys) by tapping the Power button, choosing “Lock phone” from the menu, and entering the lock code (see Figure 4-6). Once the phone is locked, you can perform only two actions:
You can tap the left soft key, which is labeled Unlock on the screen, and enter the lock code again to unlock it. If you are in the dark, tap the Power button to turn on the LCD backlight.
If there is an incoming call, the locked phone will ring and you can take the call by pressing the green Call button.
Tip
If you just want to lock your keypad to prevent accidental dialing (or launching applications) when the phone is in your pocket, you can press the left soft-key and the * key at the same time. To unlock it, just press the left soft-key (or middle soft-key on devices with three soft-keys) and the * key again. No password is needed. Accidental dialing is especially a problem for phones that have the navigation pad sticking out like a joystick (e.g., the Nokia 6600).
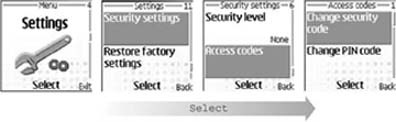
You cannot dial any phone number or execute any application when the phone is locked. The default lock code in a factory-fresh phone is 12345. You can change the lock code in the Settings → Security → Phone and SIM → Lock code menu on a Series 60 device (see Figure 4-7) or the Settings → Security settings → Access codes → Change security code menu on a Series 40 device (see Figure 4-8). On earlier Nokia Series 60 devices, you might find those settings in the Tools program rather than the Settings program.
Using the security settings, you can also configure the phone to automatically lock itself after a period of time (see the “Autolock period” option in Figure 4-7).
Protect the Memory Card
The memory card on a Nokia device can store large amounts of personal data, such as pictures and other media files. Even with a locked phone, someone can still physically remove the memory card and potentially read its contents using a card reader. You can use a password to protect the memory card so that it cannot be used in other devices or card readers.
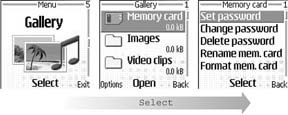
On a Series 60 device, you can lock the memory card via the Options → Set password menu in the Extras → Memory menu (see Figure 4-9). On a Series 40 device, you can set the memory card password via the Options → Set password menu when you select the memory card icon in the Gallery menu (see Figure 4-10).
Encrypt Sensitive Data
Many Nokia Series 40 and Series 60 phones include the Nokia Wallet application. On my Nokia 6600, the Wallet application is accessible via the Extras → Wallet menu. The first time you use Wallet, you will be asked to create a wallet code, which is used to generate an encryption key. Then you can store small bits of data, such as web site passwords and bank accounts, in the wallet. The data stored in the Wallet application is encrypted and is accessible only to the person who knows the wallet code. On some recent phone models, the Wallet application can also integrate with the Services browser to save information you fill out on web forms.
Tip
If you key in an incorrect wallet code three times in succession, the Wallet application is blocked for five minutes. The next three incorrect entries of the code will double the blocking time.
If you need to encrypt entire datafiles on a Nokia Series 60 phone, third-party applications such as SmartCrypto from SymbianWare (http://www.symbianware.com/product.php?id=scrypto60&pl=n6600) can help you. It encrypts any individual file on the Series 60 filesystem. Once the file is encrypted, you have to know the password to read its contents.
Restrict Calls
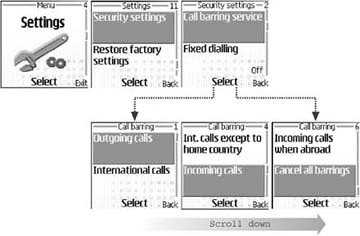
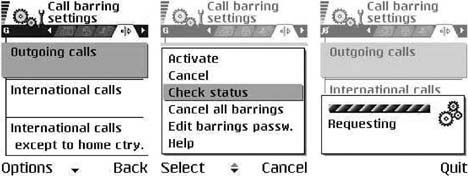
To protect against unauthorized calls, you can restrict the type of calls the phone can make or receive, via the Settings → Call barring menu on a Series 60 device and the Settings → Security settings → Call barring service menu on a Series 40 device (see Figure 4-11). For example, you can bar the phone from making expensive international calls when the device is roaming.
When you activate or remove those settings, the phone communicates with the network to update settings with the network operator (see Figure 4-12). You need to have the four-digit SIM PIN code to activate call restriction. Call your operator’s phone support and ask for the Extended Services SIM password, if you do not have it. Once you have the SIM card PIN, you can change it from the same menus you use to change the phone’s lock code.
An even more extreme measure is to restrict the phone to dial only a predetermined list of phone numbers. You can use the Settings → Security → Phone and SIM → Fix dialing menu on a Series 60 phone or the Settings → Security settings → Fixed dialing menu on a Series 40 phone to do that. You will be asked to select the allowed numbers from your Contacts list, and to enter the SIM password to activate the setting.
Report a Lost or Stolen Phone
If your phone does get stolen, the first thing you should do is call the wireless operator and deactivate the SIM card so that the thief cannot make calls against your account. You can also ask the operator to put the International Mobile Equipment Identity (IMEI) number [Hack #5] of your phone into a blacklist database. The blacklist database is a cooperative effort by wireless operators to bar blacklisted phones from making calls on any of the participating operators’ networks. This greatly reduces the value of a stolen phone. However, the current blacklist implementations have some problems:
In addition, an experienced mobile phone hacker can alter the phone’s IMEI number via data cables. It is an illegal operation, but it is possible. Once the IMEI number is altered, the phone is no longer on the blacklist.
Tip
If you live in the UK, you can register your phone with the National Mobile Phone Register via the web site http://www.immobilise.com/. This allows you to quickly report a stolen phone to the UK national blacklist and get notified when the police recover your phone.
Prevent SIM Card Changes
To prevent your stolen phone from being used by thieves, you can lock the SIM card to the phone. After you report the stolen phone and deactivate the SIM card via your operator, the thieves will not be able to insert a new SIM card and continue using the phone.
On a Series 60 phone, you can do that via the Settings → Security → Phone and SIM → Lock if SIM changed menu. Again, you will need to enter the SIM password obtained from the operator.
Tip
No solution is completely secure. An experienced hacker can still reflash your phone via a data cable [Hack #7] and get rid of the SIM lock. But the SIM lock does make it more difficult for thieves to resell the stolen phone.
Protect Your Remote Data
Protect mobile phone data on the phone’s companion PC and web accounts.
Mobile phone data is stored not only on the phone, but also on the phone’s companion PC and web accounts. For instance, the Nokia PC Suite can copy everything in the phone’s memory to a PC for offline processing or backup purposes. Voice mail messages are typically stored in the wireless operator’s voice server. Mobile web portal sites also store a lot of sensitive data from the contacts or photo albums in the Camera application. Any comprehensive mobile security solution needs to protect this remote data as well.
Secure the Companion PC
Generally, you should not use a public PC in a library or web cafe to copy data from your phone. In theory, you can delete everything off the public PC after you are done and you won’t leave a trace. But in reality, you can miss or forget to delete important data. The Nokia PC Suite can also store important information and settings (e.g., Bluetooth settings) in directories that are not obvious to most users. Hence, to avoid these potential information leaks, I recommend avoiding public PCs altogether.
You should also safeguard your PC from viruses and spyware, which can be used to steal data from your phone. A piece of good PC antivirus software, such as Norton AntiVirus from Symantec, will protect your Nokia PC Suite databases and synchronized Outlook databases from attacks.
Use Strong Passwords for Web Accounts
You should use strong passwords to protect online accounts for your mobile phone, especially the wireless operator’s web account for your service, and web sites you frequently use to share photos.
Many web services also allow users to retrieve forgotten passwords by answering a personal question (i.e., the “password question”). It is important to use a password question that is not easy to guess. And don’t forget: the answer to the question “what is your favorite pet’s name” does not have to really be your favorite pet’s name. It just has to be something you can remember.
Tip
In early 2005, it is believed that a cracker either guessed socialite Paris Hilton’s T-Mobile account password, or exploited an SQL injection vulnerability on the T-Mobile portal web site [Hack #51] and reset her password. Regardless of how the attacker did it, Paris’s account was compromised. After logging into her account, the cracker downloaded and then posted all her personal information, including her Contacts list and phone camera photos, on the Internet.
Be Aware of Caller ID Spoofing
The wireless operator’s caller ID service embeds your phone number in every phone call and every network connection you make from your phone. A common assumption is that caller ID is always accurate, since it is controlled by the wireless operator. In fact, some services even use caller ID as their primary authentication mechanism. For instance, by default, T-Mobile’s voice mail allows you to check messages without a password if you are calling from your T-Mobile mobile phone. Some web sites automatically sign into your account if you make an HTTP request from a phone number registered to your account. In many cases, your caller ID has become part of your identity.
However, in reality, caller ID is not completely secure. An experienced phone hacker can manipulate the network and change the caller ID to any number she wants—this is called caller ID spoofing. Some callback services, such as Star38 (http://www.star38.com/) and Camophone (http://www.camophone.com/), allow anyone to spoof caller ID for as little as five cents per call.
You should call your service providers and request to set passwords for all mobile phone–related network services. T-Mobile now allows customers to set an optional password on their voice mail account.
Tip
Remember that you cannot always trust the caller’s identity based on the caller ID. For instance, if you get a call with the caller ID indicating “Bank of America,” it does not necessarily mean that the call is indeed from a Bank of America representative. You certainly should not disclose your bank account information based on the caller ID. In this case, you should offer to call the representative back using a published number for Bank of America.
Get Nokia Smartphone Hacks now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.