Chapter 24. Defending Against XXE
Generally speaking, XXE is indeed easy to defend against—simply disable external entities in your XML parser (see Figure 24-1). How this is done depends on the XML parser in question, but is typically just a single line of configuration:
factory.setFeature("http://apache.org/xml/features/disallow-doctype-decl",true);
XXE is noted by OWASP to be particularly dangerous against Java-based XML parsers, as many have XXE enabled by default. Depending on the language and parser you are relying on, it is possible that XXE is disabled by default.
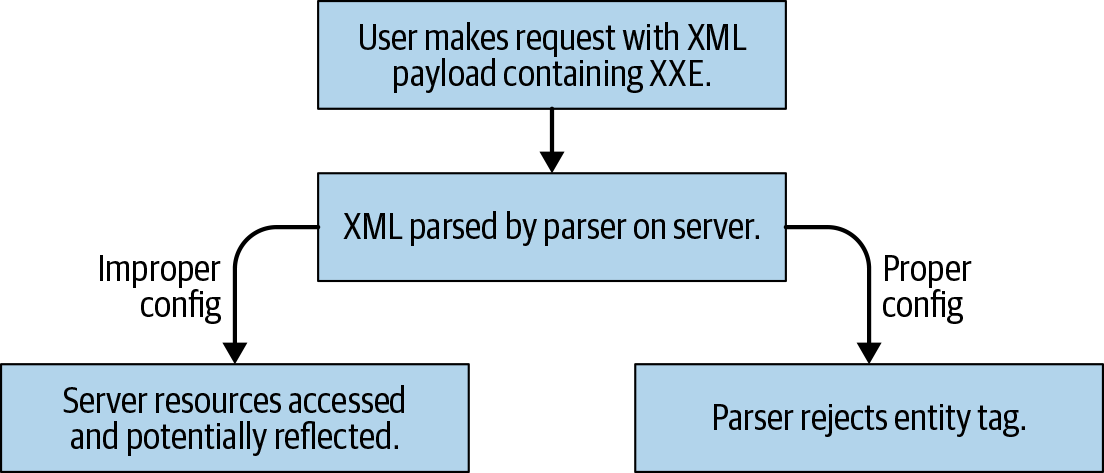
Figure 24-1. XXE attacks can be easily blocked by properly configuring your XML parser
You should always check your XML parser’s API documentation to make sure, and not just expect it is disabled by default.
Evaluating Other Data Formats
Depending on your application’s use cases, it may be possible to re-architecture the application to rely on a different data format rather than XML. This type of change could simplify the codebase, while eliminating any XXE risk. Typically, XML can be interchanged with JSON, making JSON the default when looking at other formats.
JSON, on the other hand, would not be practical if your application is parsing actual XML, SVG, or other XML-derived file types. It would, however, be a practical solution if your application is sending standard hierarchical payloads that just happen ...