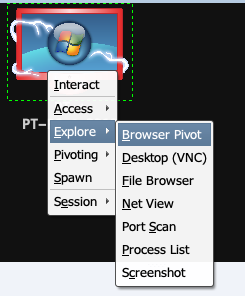
The options available in the Explore menu are as follows:
- Browser Pivot: Cobalt Strike allows us to do a man-in-a-browser attack to hijack a victim's authenticated browser session. Cobalt Strike sets up a proxy server which injects into Internet Explorer. When we browse through this server, we will be able to inherit all the cookies, client SSL certificates, and all the authenticated HTTP sessions. Let's take a look at how to perform this attack. First, right-click on the host and go to Explore | Browser Pivot, shown as follows:
This will open a new window with a list of currently running Internet explorer processes on the system. ...