Configuring User Authentication
Authenticating users early in the connection process reduces the amount of information about that can be gained regarding your IIS 6.0 solution through anonymous access. In highly-secure Web sites and applications, you need to require authentication before the user can access any of the information. For other Web sites and applications, you might require authentication only when the user is going to access portions of the Web site or application that contain confidential information.
Figure 3.5 illustrates the process for configuring user authentication.
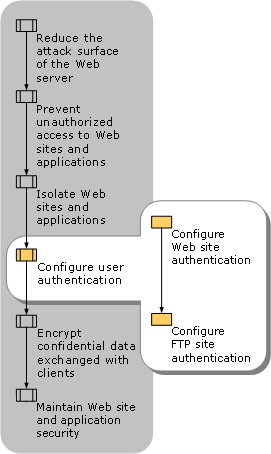
Figure 3.5. Configuring User Authentication
Based on the types ...
Get Internet Information Services (IIS) 6 Resource Kit now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

