Time for action – collecting data
Follow the given instructions to get started:
- First of all, we need a device that's looking for multiple networks. Generally, a normal smartphone such as an Android device or iPhone will do the trick. Desktops don't generally make good targets as they tend to remain in one location. Newer iPhones and Android devices may have probe requests disabled or obfuscated, so do check before you give up.
- Once you have your device, make sure the Wi-Fi is turned on.
- Then set up your monitoring interface as we have done many times before:
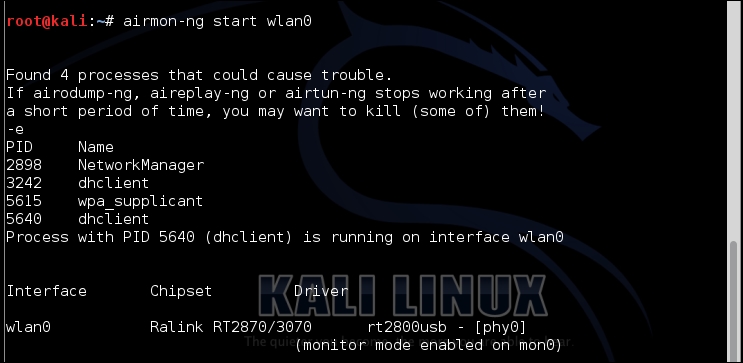
- The next thing to be done is to look for probe requests with
tsharkvia the following command: ...
Get Kali Linux Wireless Penetration Testing : Beginner's Guide now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

