June 2018
Beginner
510 pages
13h 7m
English
The following is an example of a 64-bit malware dropper (called Hacker’s Door). If you are not yet familiar with debugging 64-bit samples, refer to section 2.7, Debugging 64-bit Malware, in the previous chapter. The malware uses the same set of API functions to find and extract the resource; the difference is that the first few parameters are placed in the registers and not pushed onto the stack (because it is a 64-bit binary). The malware first finds the BIN/100 resource using the FindResourceW() API, as follows:
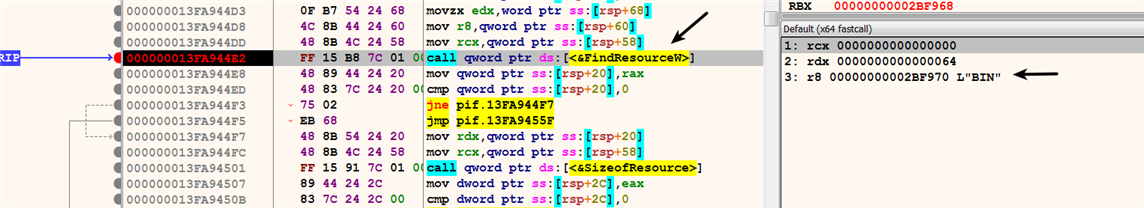
Then, the malware uses LoadResource() to retrieve the handle to the data associated with the resource, ...