June 2018
Beginner
510 pages
13h 7m
English
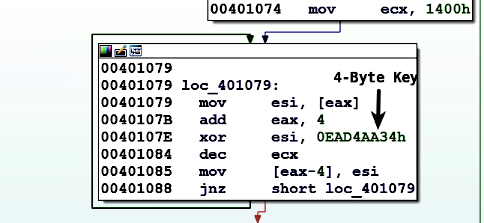
Attackers commonly use multi-byte XOR because it provides better defense against the brute-force technique. For example, if a malware author uses 4-byte XOR key to encrypt the data and then to brute-force, you will need to try 4,294,967,295 (0xFFFFFFFF) possible keys instead of 255 (0xFF) keys. The following screenshot shows the XOR decryption loop of the malware (Taidoor). In this case, Taidoor extracted the encrypted PE (exe) file from its resource section and decrypted it using the 4-byte XOR key 0xEAD4AA34:
The following screenshot shows the encrypted resource in the Resource Hacker tool. The resource can ...