June 2018
Intermediate to advanced
294 pages
7h 5m
English
On the other hand, the attacker has already accessed the same blog site and he has a different account that he uses to blog about anonymous activities on a daily basis. The attacker saw that this site is already vulnerable to Cross-Site Request Forgery using his favorite scanner, Burp. Next, he will build a malicious page to infect his victims. To build his page, he enabled the proxy/intercept in Burp to analyze the contents of the web requests. On the Intercept page, he will right-click on the request and try to generate a CSRF POC:
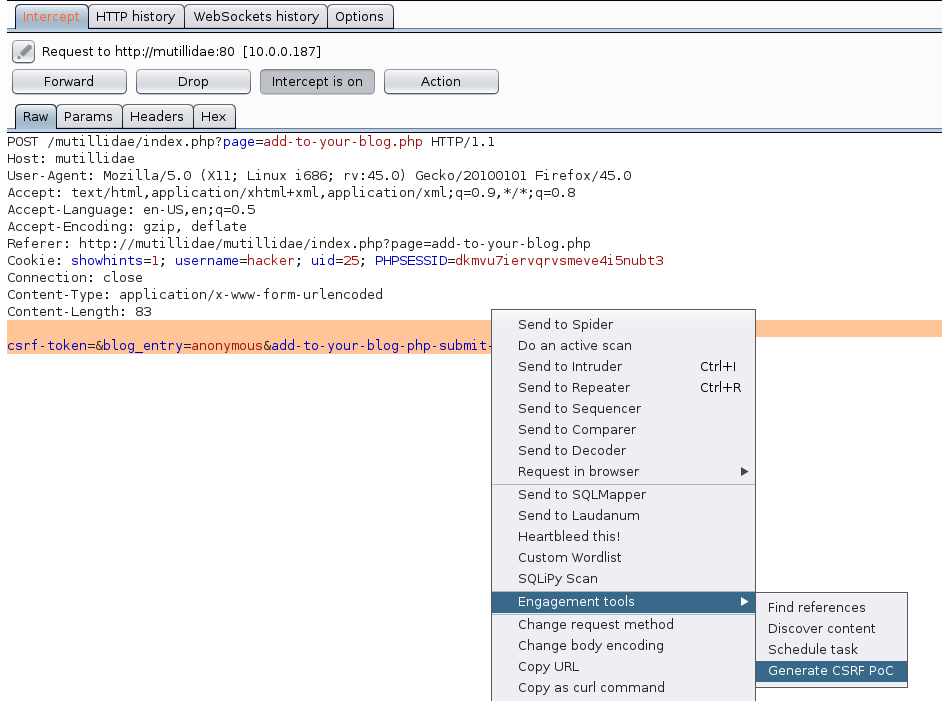
After that, a new pop-up window will show. At this moment, the attacker can take the generated ...