Another good plugin that aids in discovering hidden processes is the psxview plugin. This plugin compares the active processes indicated within psActiveProcessHead with any other possible sources within the memory image. To run the plugin, type the following command:
forensics@ubuntu:~/Documents$ volatility -f stuxnet.vmem --profile=WinXPSP2x86 psxview
The command produces the following output:
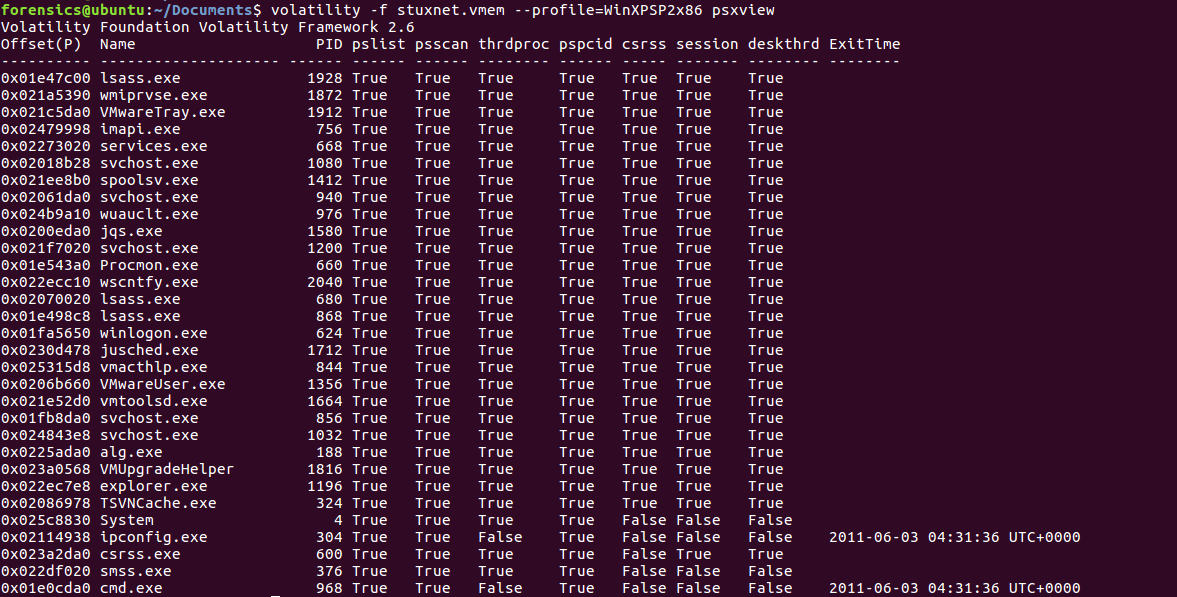
A False within the column indicates that the process is not found in that area. This allows the analyst to review that list and determine if there is a legitimate reason that the process may not be there, or if it is indicative of an attempt ...

