If you need to connect to Unix or Linux servers, you may be familiar with utilities such as Telnet and FTP. Telnet lets you connect to a command prompt on a machine over the network. The FTP utility transfers files between your machine and a remote server.
If you are using either Telnet or FTP to connect to a sensitive
server, but you’re not also using a VPN, you are
probably exposing your password to anyone who can access the network
you’re connected to (perhaps you’re
on a public network at a wireless hotspot?), the network where the
remote server resides, and any network in between. (Ever wonder what
networks sit between you and a remote computer? Use the
tracert
command at the Windows XP Command Prompt
to trace the route between your computer and a remote host, as in
tracert www.oreilly.com).
Tip
Anonymous FTP, in which you use your email address as a password, is not a concern. This is because, as the name implies, all remote users are treated as anonymous guests, and, if the remote FTP server is configured properly, are accorded no privileges that could be abused.
If the remote server supports it, you can use the Secure Shell (SSH) protocol to work with a remote machine’s command prompt (replacing Telnet) or securely transfer files (replacing FTP). SSH Communications Security offers SSH utilities for Windows and other platforms. Open source variants include openssh (http://www.openssh.org), which is included with the Cygwin (http://www.cygwin.com) distribution, a Linux-like environment for Windows. However, since Cygwin has a fairly big footprint, a popular open source alternative is PuTTY, a suite of SSH utilities that fit on a floppy disk.
PuTTY is available from http://www.chiark.greenend.org.uk/~sgtatham/putty/.
At a minimum, you should download and install (put the
.exe somewhere in your Windows PATH)
putty.exe. If you want to perform secure file
transfers, download
pscp.exe
and psftp.exe.
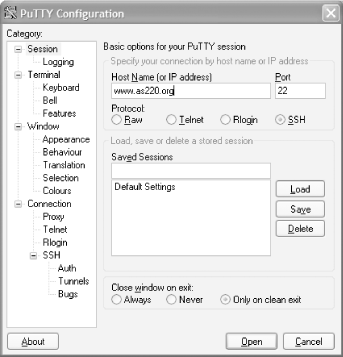
To connect to a remote host with PuTTY, launch the application, specify SSH as the protocol (the default is to use the insecure Telnet protocol), and supply the IP address or hostname of the machine to which you want to connect, as shown in Figure 4-14.
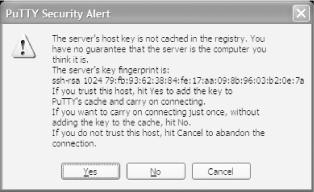
The first time you connect to a remote server with PuTTY, it will advise you that the server is unknown to it (see Figure 4-15). Click Yes or No to continue connecting, and then type your username and password when prompted to do so.
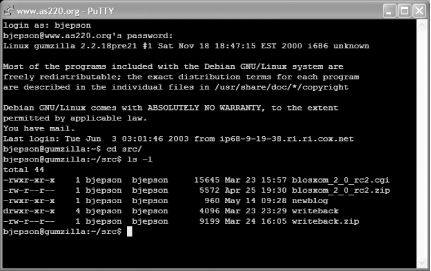
Once you are logged in, you can issue commands on the remote machine as shown in Figure 4-16.
You can use pscp (secure copy) and
psftp (secure FTP) at the Windows XP Command
Prompt. To copy a file with pscp, use
pscp
username
@
host:path,
as in pscp secret_document.doc bjepson@www.as220.org:MyDocuments/.
To use psftp, specify the hostname, and log in
with your user ID and password. You can use ftp commands such as
put (to upload a file to the server) and
get (to download a file from the server):
C:\Documents and Settings\bjepson\My Documents>psftp www.as220.orglogin as:bjepsonUsing username "bjepson". bjepson@www.as220.org's password:********Remote working directory is /home/bjepson psftp>cd MyDocumentsRemote directory is now /home/bjepson/MyDocuments psftp>put secret_document.doclocal:secret_document.doc => remote:/home/bjepson/MyDocuments/secret_document.doc psftp>get super_secret.docremote:/home/bjepson/MyDocuments/super_secret.doc => local:super_secret.doc
For more information, consult the PuTTY documentation and FAQ, located at the PuTTY home page.
Get Windows XP Unwired now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.