Chapter 6. Extended Enterprise runtime patterns 109
6.3 Exposed Direct Connection runtime pattern
When using the Exposed Direct Connection runtime pattern, the source
application uses a connector to access the target application. This allows a
single interaction from the source application to be adapted and transported to
one partner target application.
6.3.1 Generic profile
This Runtime pattern allows two different organizations to talk to each other with
a mutually agreed upon message format and protocol. Each partner can use
their own internal messaging format, then use a connector adapter to convert
from the internal format to the external format.
The connector itself can be explicitly or implicitly modeled. If the connector is
explicitly modeled, the modeler can use decomposition and abstraction
techniques to expand the connector to the appropriate level of detail.
The term
Connector can be qualified by both the connector variation and by the
interaction variation. Some examples are:
Adapter Connector
Path Connector
Message Connector
Call Connector
Call Adapter Connector
The target application relies on services provided by its hosting server. These are
modeled using the Application Server/Services component.
The Rules Directory might or might not exist. If it does exist, it is a modeling
decision as to whether the rules need to be shown in the Runtime pattern. For
example, analysis might determine that connection rules are not an important
part of the solution, so the Rules Directory might be left off the Runtime pattern.
The Directory and Security Services node supplies authentication and
authorization services. It also holds the user ID as well as password and related
privileges. This node typically leverages LDAP-based directories. It also contains
configuration information needed to support secure access between the
enterprise and partner services.
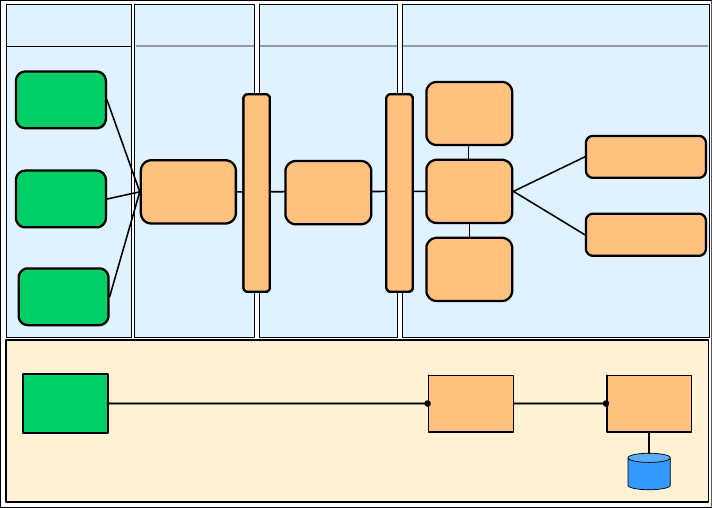
The generic profile of the Exposed Direct Connection runtime pattern is shown in
Figure 6-2 on page 110.
110 Patterns: Extended Enterprise SOA and Web Services
Figure 6-2 Exposed Direct Connection runtime pattern: generic profile
Figure 6-2 shows a standard pattern of Path Connectors (firewalls and network
infrastructure), but other variations do exist with fewer or more firewalls.
The secure zone Connector is primarily concerned with logical connection of the
Path Connector to the Application Services, and will therefore often be modeled
as an Adapter Connector.
Less secure applications and connectors can be placed within the Demilitarized
Zone, depending on local security policies. The less secure applications are
usually placed as shown in Figure 6-2.
We do not have separate Runtime patterns for the message and call variations of
the Exposed Direct Connection application pattern. It is still important to identify
that your business scenario requires a message or call application pattern
because you can use this knowledge as a consideration when selecting a
Product mapping.
Inter-enterprise
Zone
Enterprise
Demilitarized Zone
Enterprise Secure Zone
Partner Zone
App Server/
Services
App Server/
Services
Network
Infrastructure
Protocol FirewallProtocol Firewall
Connector
App Server/
Services
App Server/
Services
Domain FirewallDomain Firewall
Exposed
Connector
Rules
Directory
App Server/
Services
Directory
& Security
Services
Target
Application
Connection
Rules
Source
Application
Exposed Direct Connection

Chapter 6. Extended Enterprise runtime patterns 111
6.3.2 SOA profile
In the SOA profile for the Exposed Direct Connection runtime pattern, the
Exposed Connector, Rules Directory, and Partner Infrastructure are specialized
as shown in Figure 6-3 to instead become:
An Exposed ESB Gateway
An ESB
Service Consumers and Providers
Figure 6-3 Exposed Direct Connection runtime pattern: SOA profile
The Exposed ESB Gateway provides support for the exposed requirement of the
Extended Enterprise pattern. It provides a single point of access between:
External Service Consumers and Service Providers in the Enterprise Secure
Zone
Service Consumers in the Enterprise Secure Zone and external Service
Providers
The Exposed ESB Gateway secures the connection between enterprises and
provides namespace mapping.
The ESB meets the Connector and Rules Directory requirement of the Direct
Connection runtime pattern generic profile, but also gives support for the SOA
infrastructure by providing for service location transparency and interoperability,
Inter-enterprise
Zone
Enterprise
Demilitarized Zone Enterprise Secure ZonePartner Zone
App Server/
Services
App Server/
Services
Network
Infrastructure
ESBESBESB
Domain FirewallDomain Firewall
Exposed
ESB
Gateway
Protocol FirewallProtocol Firewall
Connector
App Server/
Services
App Server/
Services
<Service Consumer>
App Server/
Services
<Service Provider>
Directory
& Security
Services
Target
Application
Connection
Rules
Source
Application
Exposed Direct Connection
Get Patterns: Extended Enterprise SOA and Web Services now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

