Integrity
When you download a file over the Internet, you’d like to be sure that the file you get is the one you wanted; you’d like to be assured of the file’s integrity. Many people make the following assumptions, consciously or unconsciously, when they download a file from a server:
The file is not a malicious program.
The file has not been replaced, unbeknownst to the server’s owners, by a malicious program.
There is not another computer between you and the server, sending you a different file than the one you want or modifying the file that gets sent to you. This is the “man-in-the-middle” attack.
This is a hefty batch of assumptions, not stuff that gives you a warm fuzzy feeling. Although these assumptions are geared toward executable files, any type of download is at risk. You want to be sure that you get what you thought you were getting.
For example, Maid Marian runs an FTP server. One of the files she puts on it, for public consumption, is her schedule for the next couple of weeks. Journalists and paparazzi check this schedule regularly, as does Robin Hood. Robin Hood is always suspicious, so he’d like some assurance that the schedule file he downloads is not a counterfeit.
A message digest can be used to verify data integrity. A message digest is a special number calculated from a set of input data.[4] Figure 2.5 shows how this works.
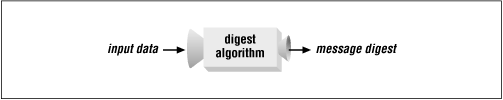 |
Let’s try to use ...
Get Java Cryptography now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

