Detecting Malicious Java Applets
Detecting a malicious Java applet without an automated detection tool isn’t easy unless you are a Java programmer.
- Disable Internet access
If you suspect a malicious Java applet, disable Internet or network access to prevent the spread of potential damage.
- Use an antivirus scanner or detection tools
Your first step after disabling Internet access should be to use a reliable antivirus scanner to look for malicious code.
- Review saved Java applets
You can list the Java applets (and ActiveX controls in Internet Explorer) that are installed with your browser. If you take the time to look, you might be surprised. Internet Explorer lists the following information about each object:
Name and type of object
Company that made the object (optional)
Size, GUID, and version
Time and date created
Time and date last accessed
Physical location of object
Package archive file it came from (i.e.,
.ZIP,.JAR,.CAB, etc.)Name spaces used for Java applets
File dependencies needed to run
To access the object list in Internet Explorer 5.x, choose
Tools
→
Internet
Options
→
General
→
Settings
→
View
Objects. You can then select an object and choose
File
→
Property to view
specific object information. Figure 10-7 shows a
list of Java and ActiveX objects stored in my Internet Explorer
browser.
Tip
Choose File
→
Show
All
Files menu options to
display all files, if offered.
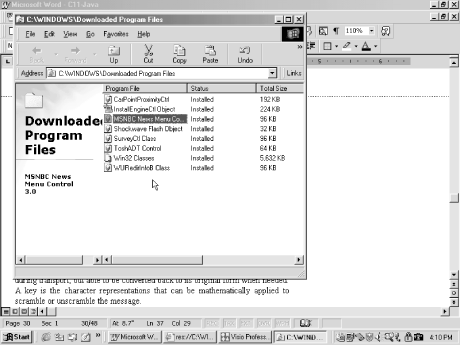
Figure 10-7. List ...
Get Malicious Mobile Code now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

