June 2020
Intermediate to advanced
382 pages
11h 39m
English
The technique presented in this section uses a type of neural network architecture called Siamese neural networks, which features two branches that share identical architectures and parameters. The use of Siamese neural networks to flag fraudulent documents is shown in the following diagram:
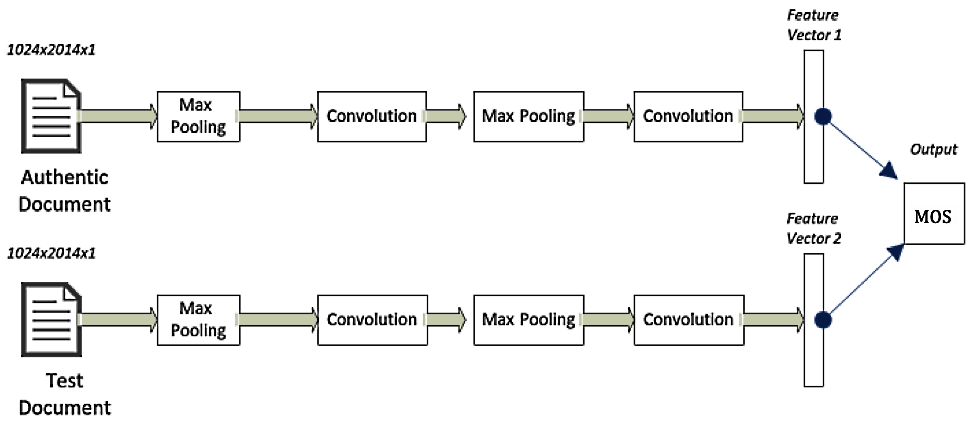
When a particular document needs to be verified for authenticity, we first classify the document based on its layout and type, and then we compare it against its expected template and pattern. If it deviates beyond a certain threshold, it is flagged as a fake document; otherwise, it is considered an authentic or true document. For critical ...