Prevent Unwanted Connections
Most Fedora systems are connected to a TCP/IP network. You can guard against unwanted inbound connections to your system by using the built-in firewall.
How Do I Do That?
To adjust the Fedora firewall graphically, select the menu option System→Administration→“Security Level and Firewall.” After you enter the root password, the window shown in Figure 8-1 will appear.
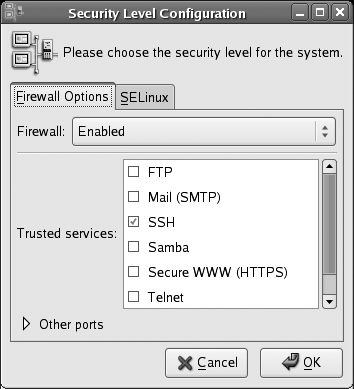
Figure 8-1. Firewall configuration tool
The control at the top of this window enables and disables the firewall. When the firewall is enabled, the lower portion of this window can be used to permit connections to your system for selected services; simply select the checkboxes for the desired services. SSH should remain selected to permit secure remote administration.
To permit connections to services that are not listed, click on the triangle for “Other ports.” The display will change to reveal an additional section, as shown in Figure 8-2.
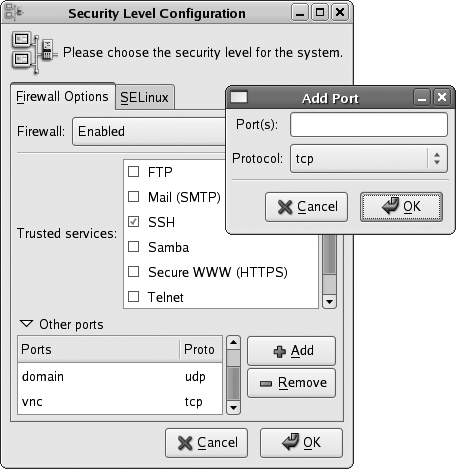
Figure 8-2. Configuring other ports
To add additional ports, click the Add button, and the window shown on the right side of Figure 8-2 will pop up. Enter the port number or the service name, select TCP or UDP for the protocol, and click OK.
Tip
A list of most of the common services and their corresponding port numbers can be found in the file /etc/services.
When the ...