2.4. Public or Asymmetric Key Ciphers
“Public” key ciphers rely on the recent (a few decades old) discovery of encryption functions with the following characteristics:
A different key is needed to decrypt information than the key used to encrypt it. See Figure 2-4.
Figure 2-4. Public key encryption
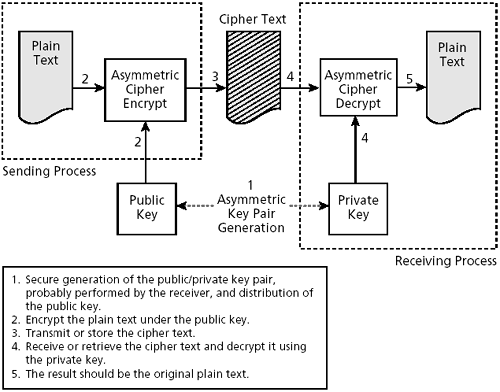
It is computationally infeasible to determine the decryption key from the encryption key.
Knowing the encryption key offers no help in decryption. Knowing the decryption key offers no help in encryption.
This set of characteristics dramatically changes the security model in comparison with secret key ciphers. Some application that wants to receive confidential ...
Get Secure XML: The New Syntax for Signatures and Encryption now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

