2.8. Enveloped Encryption
Modern public key encryption systems that encrypt arbitrary-size messages use a combination of secret key and public key ciphers. Stated more precisely, they generate a random symmetric key to encrypt each message and then encrypt that key with a public encryption key of the intended recipient. The symmetrically encrypted message is then sent along with the asymmetrically encrypted random key. See Figure 2-9.
Figure 2-9. Enveloped encryption
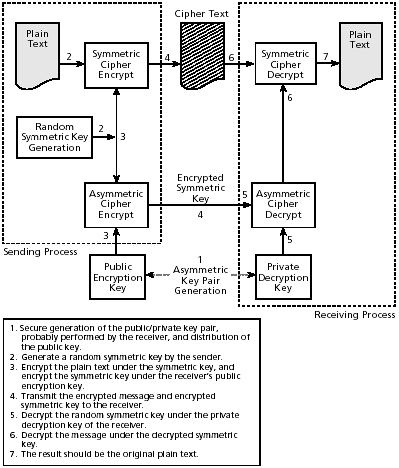
This type of encryption takes advantage of the more efficient symmetric cipher, avoiding the problem of the slowness of public key systems for large messages, while still gaining the ...
Get Secure XML: The New Syntax for Signatures and Encryption now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

