2.6. Digital Signatures
You can use public key authentication to produce “digital signatures.” These signatures have a very desirable characteristic—namely, it is computationally infeasible for anyone without the private key to produce a signature that will verify for a given message. Modern digital signatures consist of (1) a message and (2) a message digest of that message asymmetrically transformed under a private key of the signer. See Figure 2-5.
Figure 2-5. Digital signatures
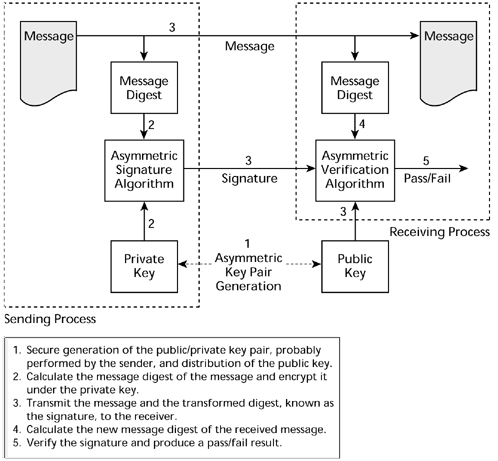
Because message digests are short, fixed-length quantities, the slowness of public key algorithms has minimal effects on processing. The critical need to be sure you ...
Get Secure XML: The New Syntax for Signatures and Encryption now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

